The FBI recently announced a potentially significant ransomware attack on the healthcare sector.
Ransomware groups are becoming more sophisticated and efficient in their ability to deploy ransomware attacks. The challenges presented by COVID-19 have only increased the target on health systems.
KLAS posed the following three questions to five CEOs at healthcare-focused cybersecurity firms:
1. What are your top three suggestions for health systems to implement immediately?
2. What are your top three suggestions for health systems to implement for the long term?
3. How should a provider organization consider reacting if they are hit by ransomware?
Below are the responses KLAS received:
Question 1: What are your top three suggestions for health systems to implement immediately?
Clearwater:
1. We recommend that organizations immediately provide and brief their security and IT staff members on the joint cybersecurity advisory regarding ransomware activity targeting the healthcare and public health sector issued October 28, 2020.
2. After the briefing and a review of the Multi-State Information Sharing and Analysis Center’s Joint Ransomware Guide available on CISA.gov, organizations should determine in conjunction with their cybersecurity and IT teams a plan for addressing the recommendations and best practices listed within the advisory and ransomware guide, prioritizing quick wins or items they can do quickly that will reduce organizational risk.
3. We recommend that organizations immediately notify their staff members that there is a threat and that they should be on the lookout for suspicious emails and that they do not open or click links within these emails and instead refer them to the appropriate IT or cybersecurity team within their organizations. When in doubt, do not open or click. Also, make sure antimalware and antivirus software is up to date.
CynergisTek:
1. Conduct a compromise assessment to look for signs of adversary activity.
2. Develop a runbook and business continuity plan for ransomware.
3. Conduct a full audit of all privileged users and their access levels and configuration.
Fortified Health Security:
1. Strategic: Stay current on available information from the Cybersecurity and Infrastructure Security Agency, the Department of Health and Human Services, the Federal Bureau of Investigation (FBI), and peer organizations such as CHIME and Health Information Sharing and Analysis Center. Monitor available indicators of compromise (IOC).
Tactical: Update all available patches to include third-party apps and ensure your endpoint security tools are updated.
2. Strategic: Inform leadership, board, and employee population of heightened threat; email phishing is the number one entry point, so your users must be educated and aware.
Tactical: Monitor and hunt for threats. Implement available IOCs into SIEM rules.
3. Strategic: Review and test incident response (IR) and communication plans and understand your cybersecurity insurance IR policy requirements.
Tactical: Make sure you have an up-to-date inventory, and test your backup or downtime plan.
Intraprise Health:
1. Increase vigilance:
a. Ensure the organization is following recommended risk management best practices including those outlined in the CISA/FBI advisory.
b. Inventory systems and user accounts to ensure least necessary service ports and privileges are available and assigned.
c. Consider increasing the frequency of HICS (Hospital Incident Command System) preparedness meetings.
2. Strengthen your defense and response capabilities:
a. Increase your focus on incident monitoring, intrusion detection while maintaining the most current system patch’s specifically for the types of malware identified in the CISA/FBI advisory.
b. Perform vulnerability and penetration testing, either internally or through a cybersecurity firm, to assess the current state of system and network security.
c. Deploy incident response tabletop and simulation exercises including all relevant stakeholders.
3. Raise awareness across your workforce:
a. Deploy a communication plan throughout the organization specifically regarding the CISA/FBI advisory. Keep the workforce apprised of developing events, as appropriate.
b. Enhance internal awareness techniques such as developing an organization-specific threat prioritization strategy to avoid “alert fatigue” so users if/when the organization is at a high alert state.
c. Put a greater emphasis on phishing exercises to identify non-compliant users and provide the appropriate training.
Meditology Services:
1. Evaluate your immediate technical exposure.
a. Review the specific attack vectors and IOCs provided by the FBI to evaluate for potential infection of the Ryuk ransomware and TrickBot malware.
– TrickBot’s presence could indicate an imminent attack. Get backups going for critical systems right away if you find TrickBot on the network.
b. Review any recent pen tests or known vulnerabilities to see whether they align with the attack vectors for Ryuk or TrickBot.
c. Accelerate any pending security patches, focusing on critical and high-risk vulnerabilities.
2. Evaluate and adjust your backup and IR operational capabilities.
a. Maintain offline, encrypted backups of data. Regularly test your backups.
b. Review IR and business continuity plans to prepare for potential attacks.
c. Get clinical and business functions prepared for downtime and potential system outages.
3. Get prepared and raise awareness internally.
a. Focus on awareness and training regarding ransomware and phishing scams, how they are delivered, and whom to contact if suspicious activity is observed.
b. Get a forensics and breach response firm on retainer if you don’t have one, and make sure you align with your cyber liability provider’s permitted firms.
c. Continue to monitor the situation. Make adjustments and communicate internally to the organizations as needed.
Question 2: What are your top three suggestions for health systems to implement for the long term?
Clearwater:
1. To move from reactive to proactive, we advise organizations to adopt the NIST Cybersecurity Framework. This framework, developed jointly by the public and private sector, is the government-recommended cybersecurity framework for critical infrastructure industries like healthcare.
2. Perform ongoing risk management as described within the NIST Cybersecurity Framework and required by the HIPAA Security Rule.
3. Regularly test both your IR and business continuity plans and capabilities.
CynergisTek:
1. Use network segmentation.
2. Utilize endpoint detection and responses.
3. Adopt multifactor authentication.
Fortified Health Security:
1. Strategic: Implement robust identity and access management program to practice least privilege access and multifactor authentication.
Tactical: Implement advanced endpoint protection and managed detection and response.
2. Strategic: Perform regular IR exercises and consider an IR retainer.
Tactical: Ensure proper and regular patching throughout the environment.
3. Strategic: Review security technologies to ensure they are properly operationalized.
Tactical: Disable all unused or unnecessary ports, protocols, and services, such as RDP.
Intraprise Health:
1. Take this opportunity to implement important controls, such as:
a. Multi-factor authentication
b. Technology that automates threat mitigation
c. Update website “blacklists” (e.g. block personal email sites)
2. Address preparedness holistically and from a risk management perspective.
a. Adopt a risk management framework (e.g. NIST RMF, HITRUST)
b. Consider implementing a Zero Trust framework
3. Incorporate Focused Security Risk Assessments into your annual security management plan.
Meditology Services:
1. Prepare and test your business continuity, disaster recovery, and IR capabilities.
a. Create, maintain, and exercise a basic cyber IR response plan and associated communications plan. Have scenarios and playbooks built out that are specific to ransomware.
b. Conduct tabletop simulations and get ready; be as prepared as possible to anticipate these attacks.
2. Invest in remediation of gaps or weaknesses in your business continuity, disaster recovery, and IR capabilities.
a. Shore up your business continuity and disaster recovery programs.
b. Evaluate network segmentation and other controls that can limit the spread and impact of malware events.
3. Build a robust and comprehensive risk management program aligned with industry standard controls. HITRUST and NIST are the most common frameworks in play for healthcare entities.
a. Conduct enterprise risk assessments, pen tests, ransomware tabletop exercises, and phishing tests on a routine basis; work your corrective action plans.
b. Prioritize focus on control areas like business continuity, disaster recovery, network segmentation, incident response, etc. that have a direct impact on ransomware prevention and response.
c. Enhance your governance and enterprise risk reporting capabilities to support informed decision making and investments from the business.
Question 3: How should a provider organization consider reacting if they are hit by ransomware?
Clearwater:
1. Follow the ransomware response checklist provided within the advisory and more fully described in the Multi-State Information Sharing and Analysis Center Ransomware Guide.
2. Contact local FBI field office or the FBI’s CyWatch.
3. Consider contacting CISA if additional assistance is needed.
CynergisTek:
1. Reach out to the FBI.
2. Review cyber insurance.
3. Activate IR retainer.
Fortified Health Security:
1. Remain calm. Focus on execution of the IR plan. Isolate the impacted machines to minimize infection. Maintain integrity by just removing them from the network, not shutting them down.
2. Notify key stakeholders, the general counsel, the C-suite, and public relations individuals.
3. Contact cyber insurance companies, vendors, and trusted partners to align resources and support your IR process.
Intraprise Health:
1. Activate your incident response plan and HICS or other command center operations. Contact and work through the appropriate authorities (e.g. FBI, local law enforcement, HHS, etc.)
a. Isolate the affected system or network(s) from the rest of your network. Up to an including an “air-gapped” state.
b. Eradicate the threat/malware.
c. Perform recovery procedures and ensure data integrity.
2. To the degree possible, minimize disruption to the current state of operations and systems to allow for proper forensics analysis.
3. Address gaps and risk that lead to the attack.
a. Perform a post-mortem and incorporate learnings into your security program.
Meditology Services:
1. Activate your incident response plan and teams. Work the plan, coordinate with the business, and make decisions based on the situation on the ground.
2. Get coordinated with the FBI and law enforcement to get the best handle on the flavor of ransomware you are dealing with.
3. Get third-party support for forensics.
Health systems are under siege.
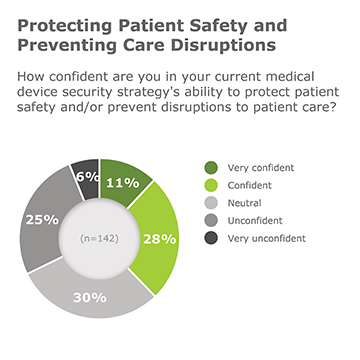
We are seeing large health systems being shut down for multiple days due to ransomware. These incidents are directly impacting patient care and safety, which have long been concerns for healthcare security leaders.
In 2018, KLAS surveyed health security leaders about their medical device security programs. Almost two-thirds of respondents reported they were not confident in their ability to protect patient safety and prevent care disruption.
Just last month, longstanding concerns that security incidents could impact patient safety were realized when a patient in Germany was lost due to a ransomware attack.
How will the increasing prevalence of ransomware and other forms of cybersecurity attacks impact health systems’ prioritization around building robust cybersecurity programs and budgets in healthcare?
For more information regarding the FBI announcement, you can refer to their website. For questions regarding this blog and healthcare security, please contact us.
Originally posted on www.klasresearch.com (https://klasresearch.com/blog/dealing-with-ransomware-attacks-in-healthcare-5-ceos-respond/808)
November 4, 2020
By Kaleb Harris