
BluePrint Protect™: Healthcare Risk Management Software
Identify and Remediate Vendor Risk with Software and Expert Services

Security Workflow Automation
BluePrint Protect™ drives task management and reporting to accelerate milestone completion, reducing the time and burden for all involved — especially your security team.

Enterprise Risk Visibility & Decision Support
Visualization tools and dashboards provide a comprehensive, ongoing and dynamic view of enterprise-wide risks (internal or third-party).

Accountability Across All Users and Assessments
Security team members, internal colleagues and third-parties can access or connect to the BluePrint Protect™ software platform to collaborate and communicate in real time.
BluePrint Protect™ TPRM Software
Through a combination of industry leading technology and our award-winning healthcare cybersecurity experts, the BluePrint Protect™ software platform solves three fundamental issues our customers face every day: lack of resources, expertise “drain” and an inability to scale against ever increasing cyber threats and regulatory requirements.
BluePrint Protect™ allows users to:
- Automate and accelerate key Information Security Office functions
- Streamline day to day security processes
- Visualize enterprise risks more clear
Complete Third-Party Risk Assessments 3x Faster
Using BluePrint Protect’s™ innovative third-party risk management software, client stakeholders, assessors and third-party response teams collaborate in real-time to accomplish security program functions driven by pre-configured rules-based prompts, alerts, and notifications. BluePrint Protect’s™ proprietary Third-Party Risk Management software workflow provides transparency and real-time reporting of assessment status while enabling multi-user access and parallel-processing of risk assessments leading to 3x faster completion time on average. BluePrint Protect™ helps manage third-party risk.
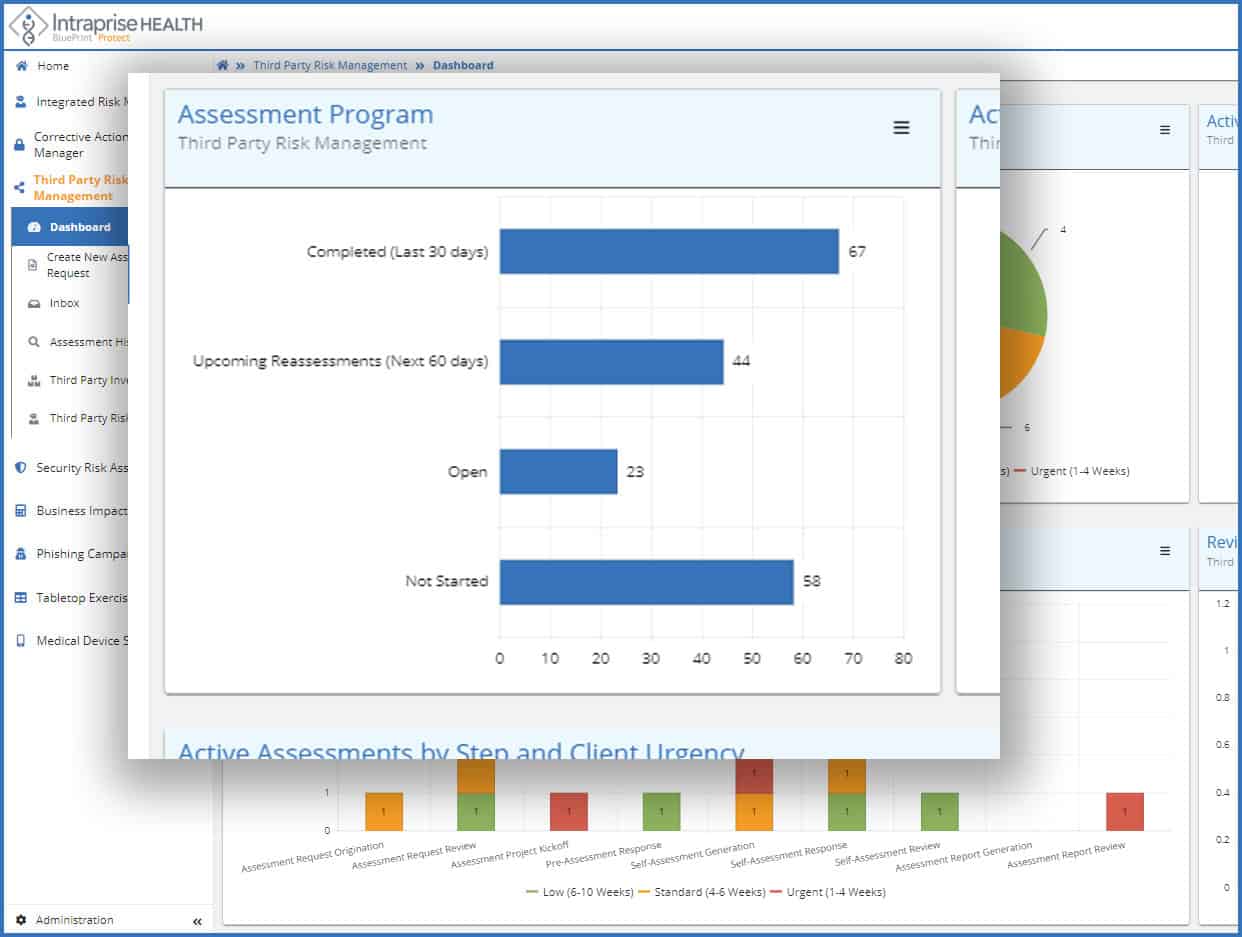
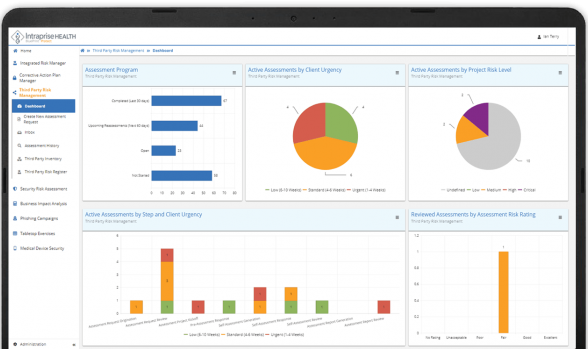
Assessment Program
- Establish repeatable, third-party risk management program
- Vendor profiling (across supply chain)
- Automated tiering
- Dynamic vendor risk assessment questionnaire (no more “one size fits all”)
- Receive real-time views of your third–party risk assessment program throughput as well as reassessments in the queue allowing you to better meet your organization’s TPRM strategy
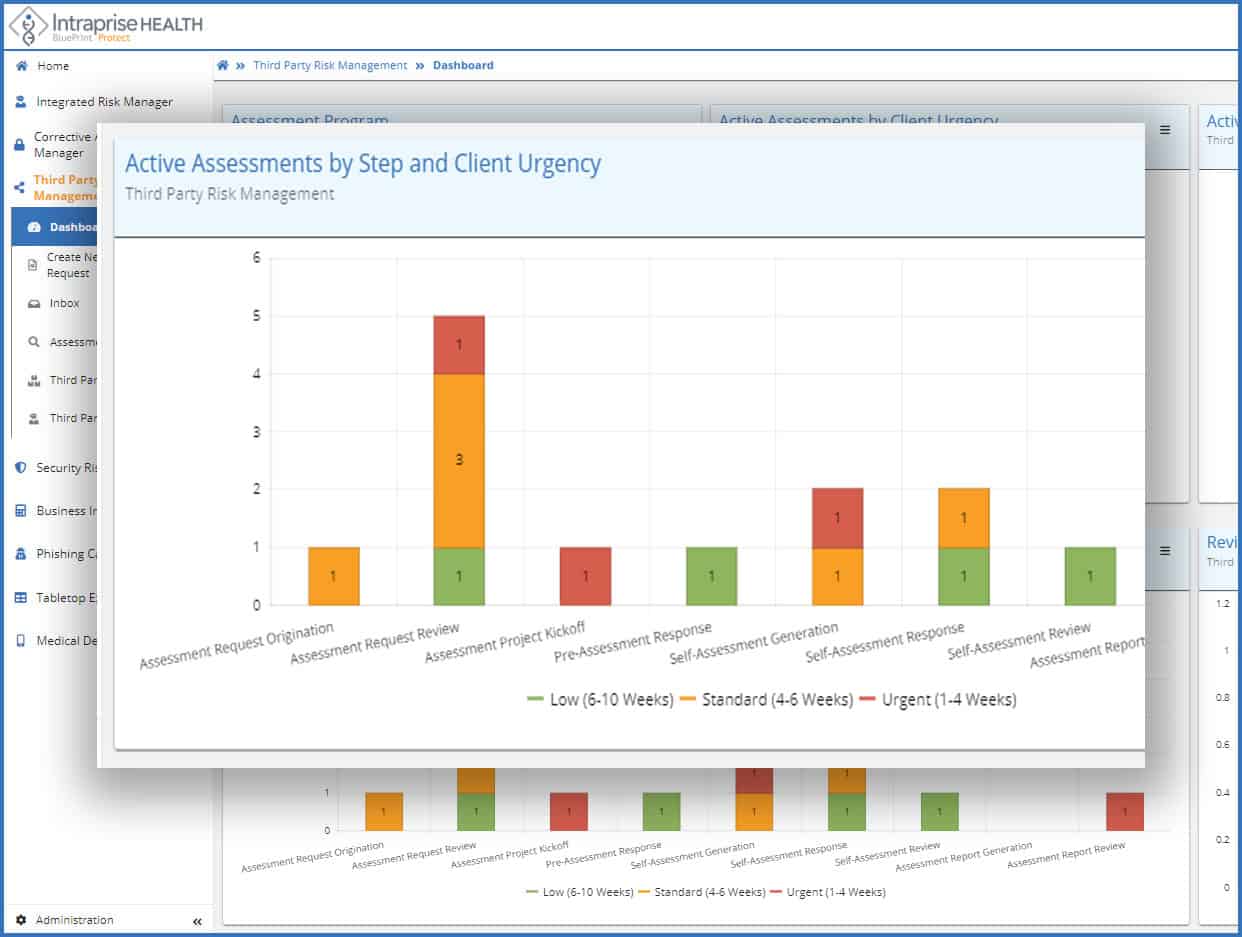
Active Assessments by step and client urgency
- Give users transparency as to overall security assessment process
- Understand potential throughput bottlenecks
- Proactively take action on in-process assessments with BluePrint Protect’s™ built-in collaboration features and automated reminders
- Ensure your highest priority vendor risk assessments are completed in support of your business needs
TPRM as part of your Integrated Risk Management Program
- Integrate TPRM into your overall enterprise risk management program and assessment processes
- BluePrint Protect™ utilizes the industry standard NIST RMF data model to normalize risk data and automate assessment processes to provide decision-makers and security managers with a holistic view of their risk management program status
Key Features of BluePrint Protect™ Healthcare Risk Management Software
Collaboration
BluePrint Protect’s™ collaboration features allow for better task management and faster completion times by bringing platform users together in a shared worked space with a set of robust, easy to use tools. On-line, in-band-communication features and real time documentation tools allow users to work in parallel to efficiently complete their work.
On-line Communication
Centralized communication on the platform happens with a robust set of easy-to-use tools. For instance, online chat features are used when assessors and third-party responders need to collaborate to complete an assessment. This eliminates a multitude of back-and-forth emails clogging up everyone’s inboxes through a log of all conversations which are easily referenced and have context. Information and documents can be posted and uploaded to be accessed and shared as and when needed.
Real time collaboration
Another key feature informed by our security team is the ability to enter notes, findings and commentary directly into the assessment workspace (visible only to users with proper permissions). This real-time collaboration feature creates greater alignment between our customers and our services team. Assessment and report notes highlight, in real time, potential areas of concern or actual risks so they can be addressed or mitigated as quickly as possible without “falling through the cracks,” a refrain we hear too often. Keeping notes during the course of an assessment also accelerates the completion of a Report of Findings once the assessment is complete.
Task Management
User-specific work queues contain tasks that have been assigned either automatically based on workflow and rules or by a team member. This task management feature allows users to focus on specific tasks that are open and require attention through email and platform notifications. Any user whether a customer’s security team member, an Intraprise Health security SME, an organizational stakeholder (e.g. business or system owner) or external third-party has a work queue by which to manage their open tasks.
Dashboards
Clear and easy to understand dashboards are a central feature of BluePrint Protect™ and are visible at various levels of the platform. Program-encompassing dashboards illustrate the performance of the security program in real-time. Risks are ranked by criticality and are clearly visible to the security team. Module-level dashboards show progress and performance of specific programs such as TPRM. There are also workflow dashboards which show the progress at milestone stages and by risk severity. Risks can be captured from external sources through various methods to correlate trends, aggregate risks, further enhance analysis capabilities and drive workflows such as remediation management.
Third-Party Portfolio Manager
BluePrint Protect’s™ Portfolio Manager integrates the NIST RMF 2.0 standards into an automated assessment workflow by identifying and evaluating all third-parties and their associated applications, services and hardware devices for potential impact to the organization ultimately creating a single source of truth for a client’s third-party security program.
Users can view a complete third-party assessment history, initiate new assessments, schedule future re-assessments, or add historical assessment data from internal and external sources. Portfolio Manager’s cloud-based functionality also captures supporting audits and or certifications such as HITRUST, HIPAA, ISO or SOC2 which can be shared and leveraged across the entire BluePrint Protect™ client base.
Analyzing whether the application or service contains covered or other sensitive information critical to the operation or the organization, users can then determine which third-party systems present the highest potential risk and require additional assessment, or should be scheduled for a re-assessment.
BluePrint Protect™ Risk Management Software Delivery Models

Managed Services
Third-party risk assessments are performed and managed by our TPRM services team. Findings, assessment status, queue management and program metrics are available via BluePrint Protect™ dashboards to your team.

Hybrid
Your internal team and our security experts utilize BluePrint Protect™ for assessment completion. Offload a portion of your assessments to our team and complete the rest in-house. Collaboration between the teams is centralized on the BluePrint Protect™ platform.

Self-Service
Your internal team utilizes BluePrint Protect™ to conduct assessments, interacts with third-party vendors and manages your TPRM program. We provide technical, process, and program support to your team.
Healthcare Cybersecurity Challenges
Third-party/vendor risk
Prevalence of Data
Increase in Data Breaches
Diffusion of Responsibility
Lack of Expertise / Resources
News
Intraprise Health platform strengthens healthcare security
Intraprise Health BluePrint Protect can help detect, manage security risks
Intraprise Health Launches Software Service to Battle Security Breaches in Healthcare Organizations
BluePrint Protect™ is a unique software and service delivery platform designed to solve some of the biggest cybersecurity challenges that hospitals, health systems, payers and their third-party vendors must deal with today and into the future. It’s the first-ever healthcare-focused workflow automation and visualization platform designed by certified healthcare cybersecurity professionals for CISOs and their security teams.