Hospitals and healthcare providers carry a heavy load when it comes to security: not only is patient data among the most sought-after resources for cybercriminals, but it is also among the most heavily regulated areas of cybersecurity.
These issues are exacerbated by:
- Complex digital supply chains: A medium-sized hospital system operates several hundred software packages and hundreds of different types of connected medical devices.
- Large workforces: These hospitals manage access to their systems for thousands of people and may have hundreds of owned medical practices, imaging centers, hospice facilities, home health locations, and other subsidiary entities that support a patient’s full care lifecycle needs.
The net result?
Health systems routinely struggle to assess physical access risk, cybersecurity risk, and regulatory compliance. Many put assessments off for months or even years – leaving a lot of room for hidden vulnerabilities that lead to expensive data breaches. And those that do undertake regular assessments are often overwhelmed with the volume of data they generate.
This article ensures you avoid these problems, offering a step-by-step guide to help you run both HIPAA security assessments (SRA) and privacy breach assessments (PBRA).
Expect to learn:
- Why regular cybersecurity assessments are essential for every hospital
- Everything required to undertake a successful HIPAA SRA
- How cybersecurity performance goals (CPGs) will change the future of assessments
Why Are Cybersecurity Assessments Essential for Hospitals?
There are two core reasons every hospital must undertake regular cybersecurity assessments:
- Regulatory compliance: HIPAA SRA/PBRA assessments form the minimal regulatory assessment needed in today’s environment. Failing to submit your annual SRA can lead to audits and fines from the OCR.
- Security visibility: Assessments form the foundation of any effective cybersecurity program. How can you prioritize and remediate risks without first gaining a clear view of your existing system?
Organizations that don’t assess their security posture are essentially operating in the dark: they are more likely to breach regulations, waste their cybersecurity budgets, and experience an attack because vulnerabilities were overlooked.
What is the Aim of a Cybersecurity Risk Assessment?
The fundamental aim of any cybersecurity assessment is to gain a deeper understanding of your existing cybersecurity posture; identify weaknesses which could be exploited or lead to regulatory breaches; and determine which of those weaknesses is most urgent. You will generally be assessing three core factors:
- Data protection: How well guarded is your PHI from all forms of unauthorized access and confiscation?
- Cybersecurity solutions: Which technical safeguards are in place to protect applications, networks, user access, and parent/child entity access?
- Protocols: What policy and procedural safeguards do you have in place to ensure the faithful execution of company security and privacy practices from user onboarding/offboarding to patch release management and everything in between?
To better illustrate this, let’s walk through the most common cybersecurity assessment for hospitals – a HIPAA SRA.
Five Steps to Complete Your HIPAA SRA and PBRA Assessments
The process of completing the assessment is almost identical across the commonly used methodologies:
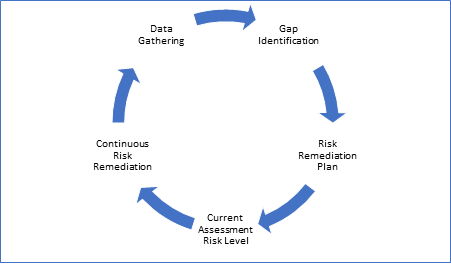
Let’s discuss these steps, with some suggestions.
1. Data Gathering
It is important to collect enough information across all three areas to capture “enough” of your system’s current state.
How much is enough? It depends. There are a series of considerations that drive the answer:
- Where do you perceive your greatest risk?
- Have there been past breaches?
- What are the most vulnerable access points?
- Have new applications been implemented?
- Has new functionality been deployed throughout your care team network?
- Will you conduct a data sample or an entire population?
Your Cybersecurity partner should be well-versed in healthcare technology, operations, regulation, and business risk in order to help you navigate these decisions.
2. Gap Identification
Based on the data collected:
- What are your gaps compared to the benchmark set for the method you are using?
- How significant are these gaps in terms of size, number, and perceived impact?
- Based on the severity and number of gaps, can you put them in a list ordered by urgency and priority?
3. Risk Remediation Plan
Take your list from step 2 and analyze the expense, effort, skills, and time needed to address each gap.
Now that you have this analysis, discuss the relative risk improvement, available budget, and available talent sources to formulate a plan of when you will address these risks.
4. Current Risk Level
Even though you have a plan, you have not executed or fixed the identified gaps yet.
As a result, you have a current risk level and a planned set of steps to fix the most important identified risks.
This is where you can engage with stakeholders to gain their alignment on all your work thus far so that the leadership team is fully aware of the organization’s current risk level, the most important steps needed to improve, and the needed investment/changes to achieve the planned improvement.
It is also very helpful at this stage if you can have some comparative data to help your leadership team understand how your risk compares to similarly situated organizations.
5. Continuous Remediation
Cybersecurity Performance Goals (CPGs) and the Future of Assessments
HIPAA SRAs and PBRAs are essential to maintain compliance, but they are far from the only assessments you should be undertaking. As both the volume and cost of healthcare cyberattacks grows, organizations should consider how they can make a wider range of assessments part of their “always-on” cybersecurity program.
The HHS’s cybersecurity performance goals (CPGs) may prove an inflection point in this regard. While currently not legally mandated, there is plenty of scope for these standards to become enshrined in regulation. Most hospitals will have to radically adapt their existing IT systems to accurately and efficiently assess whether they are meeting these goals – with a serious emphasis on storing, sharing, and analyzing assessment data.
Don’t Get Overwhelmed with Assessment Data
Given the range of systems, hardware, facilities, and software that you must assess, it is likely that you will have a fragmented collection of risk assessments (and remediation needs) for all these different parts of your organization that you must protect.
This is why 16,000+ providers rely on HIPAA One® – our complete automation software that streamlines assessments, prioritizes risks, and generates a comprehensive remediation plan. With this information, a security team can keep its stakeholders fully informed on the entire security improvement program with real transparency and accountability across the leadership team.
Want to see it in practice?
