
Case Studies & Infographics

The Importance of Policies and Procedures in Healthcare
From addressing the rise of AI within healthcare to meeting the HHS’s cybersecurity performance goals (CPGs), there has never been a better time to update your cybersecurity policies and procedures. Simply revisiting these core documents and refreshing them to meet the latest risks can immediately improve your posture – and…

TPRM Frameworks: How to Develop the Right Model for Your Healthcare Organization
Healthcare organizations can greatly benefit from improved third-party risk management (TPRM) processes. But what is the fastest and most impactful way you can achieve that goal? For many experts, the answer is clear: implement a TPRM framework. This article explores what that means and how you can select the best…

CISO vs vCISO: How Healthcare Organizations Are Adapting Security Leadership to Fit Their Stage of Growth
Limited budgets and internal expertise do not have to hold back healthcare cybersecurity. Every organization operating today can dramatically improve its security posture by developing a core strategy that guides daily activities and coordinates different areas of the business. This article explores how a virtual chief information security officer (vCISO)…

A Guide to New York’s Healthcare Cybersecurity Regulations: What Are the Requirements for Affected Organizations?
The New York State Department of Health (DOH) has published a new cybersecurity regulation (10 NYCRR 405.46) – and it represents a major turning point for healthcare entities. Hospitals and health systems within the state must now implement a range of measures to reinforce protections for patient data: In this…

How to Prevent a Healthcare Data Breach in 2025: The 80/20 Rule for Security Leaders
Healthcare leaders have never been in a better position to improve their security posture. With more executive support for cybersecurity and a clear mandate to upgrade digital defenses, it is the perfect moment to protect patient data and reinforce your approach to risk management. But what exactly should leaders focus…

New York’s Healthcare Cybersecurity Regulations: What They Mean for The Wider Industry
New York recently became the first US state to introduce comprehensive cybersecurity regulations aimed at strengthening data protection within the healthcare sector. However, while these measures only affect hospitals and health systems within New York State, our experts are confident they represent the future of healthcare cybersecurity compliance. Healthcare organizations…

Debunking Common Myths About the HIPAA Security Rule Proposal
The HIPAA Security Rule has long been a cornerstone of healthcare data protection, and with the recently proposed updates, there’s been a flood of speculation—and misinformation—about what these changes really mean. To cut through the noise, we’re debunking some of the most common myths surrounding the proposal and what it…

How Will AI Impact Healthcare Cybersecurity?
The rise of artificial intelligence (AI) is a double-edged sword for healthcare. Many claim it can revolutionize care and enhance security systems, while others consider it the biggest financial and operational threat the industry faces in 2025. This can be disorientating for healthcare leaders: Will AI protect their IT systems…

Closing the Security Gaps: What Healthcare Organizations Can Do Now to Prepare for HIPAA Changes (Part 3 of a Series)
The clock is ticking for healthcare organizations as the proposed changes to the HIPAA Security Rule loom on the horizon. While the updates are not yet finalized, they represent a seismic shift in healthcare cybersecurity, demanding proactive measures to meet stricter requirements. Organizations that act now won’t just get ahead…

Enterprise Risk Management in Healthcare: A Complete Guide for Executives
Recent surveys identified 10 different high-priority risks US healthcare organizations face. However, security leaders can tackle these challenges efficiently and effectively by adopting a unified approach that views cybersecurity risk through a single comprehensive lens. Enterprise risk management (ERM) offers a framework to help guide that process. With a unified…

From Compliance to Resilience: How HIPAA Security Rule Changes Could Impact Healthcare Providers (Part 2 of a Series)
The proposed HIPAA Security Rule changes aren’t just another set of regulations to check off—they signal a shift toward a security-first culture. In today’s hyper-digital world, where everything from patient records to care delivery is interconnected, resilience has become the new gold standard. These proposed updates challenge us to think…

What’s Changing and Why: A Breakdown of the Proposed HIPAA Security Rule Updates (Part 1 of a Series)
The healthcare industry is at a pivotal moment in its approach to cybersecurity. The U.S. Department of Health and Human Services (HHS) has proposed sweeping updates to the HIPAA Security Rule—the first significant revision since 2013. These updates aim to address the realities of modern cyber threats, from ransomware attacks…

Understanding the TPRM Lifecycle: How Healthcare Cybersecurity Teams Manage Evolving Risk
Third-party risk management (TPRM) is a major blind spot for most healthcare cybersecurity programs. Over 50% of vendor contracts are signed without enough pre-contract due diligence to identify potential vendor risks, which helps explain why the industry has experienced a 300% increase in vendor-related breaches since 2021. However, this also…

Understanding the NIST CSF Framework for Third-Party Risk Management
60% of healthcare organizations say their third-party risk management (TPRM) program needs improvement, with a recent survey showing that vendor threats keep businesses from reaching their organization goals. Third-Party Vulnerabilities and Risks Most current data breaches are partially or fully attributable to third-party risks, resulting in expanding third-party risk profiles. …

Choosing the Right Healthcare Cyber Risk Remediation Products and Services: Your Expert Guide
Many healthcare security leaders know their organization has hidden vulnerabilities that could be exploited any day now – but they lack the resources to efficiently deal with those threats. That is why cyber risk remediation solutions are so important to ensure you avert crisis and keep your patients and reputation…

Why is Healthcare Frequently the Target of Ransomware Attacks? Proven Steps to Mitigate Risk
Every healthcare executive knows that ransomware is a constant threat. But why is the industry such a prominent target for these attacks – and what can you do to curb the threat in 2025? This article tackles those questions head-on and provides a complete overview to help healthcare executives: The…

From Compliance to Collaboration: The CPO’s Expanding Role in Cybersecurity
The Evolving Role of the Chief Privacy Officer in Cybersecurity As data privacy concerns grow and cyber threats become increasingly sophisticated, the Chief Privacy Officer (CPO) is playing an essential role alongside the Chief Information Security Officer (CISO) in safeguarding organizational data. Traditionally responsible for managing data privacy and regulatory…
Robust Cybersecurity Risk Management in the Healthcare Ecosystem with George Pappas Intraprise Health on the Empowered Patient Podcast with Karen Jagoda
George Pappas, CEO of Intraprise Health, joins Karen Jagoda, host of the Empowered Patient Podcast, to discuss the complex cybersecurity challenges in healthcare, largely due to outdated and diverse IT systems. George explains, “The net situation is that these large technology companies that serve healthcare and hospital systems and large…

Exploring the Importance of the NIST Cybersecurity Framework (CSF) in Healthcare
Healthcare organizations understand they need to improve their cybersecurity and risk management processes – but most struggle to establish a consistent approach to these challenges. That is why industry experts promote the NIST cybersecurity framework (CSF) as an essential tool for healthcare organizations. With robust guidance across five key “functions,”…

Is Integrated Risk Management the Best Approach for Healthcare Cybersecurity?
From the Change Healthcare attack to the increased enforcement of penalties for HIPAA breaches, the last year has sent a clear message to healthcare leaders: a refreshed approach to risk management is needed. But what exactly should that approach look like? And do emerging models like integrated risk management (IRM)…
Podcast Healthcare De Jure: George Pappas, CEO at Intraprise Health
George Pappas, CEO of Intraprise Health, a Health Catalyst company, joins Matt R. Fisher, host of the Healthcare de Jure podcast, for an in-depth discussion on the evolution of healthcare cybersecurity beyond regulatory compliance. As cybercriminal threats escalate and the cost of breaches continues to rise, George shares strategies for…

What Are the 3 Rules of HIPAA? Understanding HIPAA Compliance
The Office for Civil Rights (OCR) has dealt nearly $6 million1 in fines for HIPAA non-compliance in 2024. However, for many healthcare cybersecurity teams, the regulations are highly complex, and the “three rules” of HIPAA are still unclear, making a violation far more likely.highly complex and the “three rules” of…

HIPAA Penalties: Understanding the Consequences of Non-Compliance
The Health Insurance Portability and Accountability Act (HIPAA) is a critical part of any healthcare organization’s compliance program. From annual security risk assessments (SRAs) to ongoing remediation efforts, healthcare cybersecurity teams are heavily occupied with these regulations. However, many organizations are still not sure exactly what the risks of non-compliance…

Common HIPAA Violation Examples: Avoiding Compliance Mistakes
Few phrases fill healthcare professionals with more anxiety than “HIPAA violation.” From public disgrace to seven-figure fines, the last few years have shown just how serious non-compliance can be for organizations and individuals – and given us plenty of examples of what a HIPAA violation looks like. But what are…

HIPAA Technical Safeguards: Are You Meeting the Requirements?
There’s a good reason the term “HIPAA headache” resonates with healthcare cybersecurity teams: the sheer complexity of the regulations can make it hard to even know whether your organization is currently compliant – let alone do anything about potential breaches. One of the biggest contributors to that complexity is the…

The Future of Healthcare Cybersecurity: Three Crucial Insights from Intraprise’s Interview with This Week Health
With the threat from cybercriminals growing and the cost of breaches rising, healthcare cybersecurity is no longer just a question of compliance – it is a matter of patient and organizational safety. This Week Health recently brought George Pappas, Intraprise Health CEO, and Scott Mattila, Intraprise Health CSO, onto their…

Healthcare Cyberattacks: Five Underestimated Risks for Covered Entities
Change Healthcare’s billion-dollar ransomware attack has woken many leaders up to the urgent necessity of stronger cybersecurity. But most media reports focus on only a handful of high-profile risks – and obscure many other urgent threats to healthcare cybersecurity. This article redresses that imbalance, exploring five underestimated risks healthcare cybersecurity…

A Healthcare Security Executive’s Guide to TPRM Software
The healthcare sector’s long-overdue digital revolution has enhanced patient care, communication, and organizational efficiency. But the transformation came with a hidden cost – and leaders have only recently begun to pay it sufficient attention. Large, complicated digital supply chains offer the perfect opportunity for cybercriminals to infiltrate healthcare systems and…

Executive Guide: Healthcare Risk Management 101
The healthcare industry is undergoing a cybersecurity reckoning – and executives are finally taking proactive steps to tackle the evolving and looming threat of cybercrime. The average healthcare organization has increased cybersecurity headcount by 30% since 2019, with the security’s share of the IT budget growing from 5% to 7%…

Six Essential Risk Management Tools in Healthcare Cybersecurity
The healthcare industry is experiencing a long-overdue digital revolution. 74% of American patients used telehealth in 2023, while the size and value of the Internet of Medical Things (IoMT) is projected to grow nearly 600% by 2032. But this rapid transformation presents a challenge for cybersecurity leaders. More interconnected digital…

A Wake-Up Call for Enterprise Healthcare: Why Proactive Cybersecurity is Mission-Critical
When a cyber-attack forced Change Healthcare to shut down 111 different services and pay a $22 million ransom in early 2024, it sparked enough outrage to prompt an investigation from Congress. This was one of America’s largest health information exchange (HIE) platforms, responsible for roughly a third of the country’s…

Third-Party Risk Management in Healthcare: Everything You Need to Know
Third-party vendors are the Achillies heel of healthcare cybersecurity. As providers have become more aware of cyberthreats, attackers have changed tactics. Rather than attempting to access data from hospitals directly, a growing number of criminals target third-party vendors whose products are integrated within these organizations’ digital ecosystems – and often…

5 Essential Steps to Create a Formalized Healthcare Cybersecurity Risk Remediation Plan
Cybersecurity remediation management could be summed up in a single phrase: clarity is power. With clear instructions and a deep understanding of the goals, risks can be addressed and resolved quickly and effectively; without them, budgets overrun, teams miscommunicate, and the entire process can last months longer than necessary. That…
Improving Security Posture with Integrated Risk Management (IRM): 6 Vital Takeaways from Our Webinar
With the growing complexity of risk assessments and changing healthcare compliance regulations, IT and Security leaders are looking for a new approach that acknowledges the true business impact of cyber threats within healthcare organizations – and our recent webinar explored integrated risk management (IRM) as a perfect way of achieving…
Why Healthcare IT Expertise Is Crucial to a Quality Penetration Test for Covered Entities and Business Associates
With the increased severity and frequency of all forms of cybercrime, it’s not surprising that the demand for penetration testing as a preventative measure has grown enormously. Properly done, a penetration test can provide a valuable overview of where vulnerabilities exist that can be exploited by hackers – and give…
5 Crucial Ways to Drive Urgency Around Cybersecurity Remediation
Navigating cybersecurity in a healthcare organization can feel like being a lookout aboard the Titanic: you can see the iceberg coming, but how do you convince the captain to change course? This blog offers insights to help leaders clarify the true threat of cyberattacks and build urgency within the c-suite.…
How Healthcare Enterprises Can Deliver Efficient Remediation Across Their Entire Network
Every enterprise healthcare organization understands the importance of cybersecurity, but few have robust processes in place to efficiently remediate vulnerabilities or adapt to future challenges. This puts them at serious risk in 2024. Security and data breaches impose costs vastly surpassing regulatory fines, with our clients reporting they’ve experienced liabilities…
How to Prepare Your Organization to Avoid Vulnerabilities in 2024
Remediating cybersecurity vulnerabilities is not something for your “to-do” list – it is an urgent priority in 2024. The average healthcare data breach costs nearly $11 million, and given that figure has steadily risen over the years, it is likely to become even more expensive this year. But fixing…
Devising Your plan for HIPAA Remediation Post-SRA
Completing your c is an important step towards maintaining compliance, but you cannot stop there. Data breaches from exploited credentials require an average of 341 days to be contained and remediated. So you need to start fixing any vulnerabilities discovered in your 2023 SRA now to avoid…
The National Health Emergency Ended 6 Months Ago: HIPAA Compliance Can No Longer Wait
The Biden administration officially ended the COVID-19 Public Health Emergency (PHE) over six months ago. But many healthcare enterprises still have not addressed the implications this has on HIPAA compliance. During the pandemic, the Office of Civil Rights (OCR) announced a range of exceptions and waivers to help healthcare…
6 Recent HIPAA Breaches (And How to Make Sure You’re Not Next)
A recent wave of HIPAA security breaches has sent a clear message to the healthcare industry: regardless of a covered entity’s size or presence, the reputational and financial risks associated with any form of non-compliance are simply too big to ignore. And with the number of cybersecurity incidents reported to…
4 Ways Assessors Make Your HIPAA SRA Painless
Every healthcare covered entity must complete their HIPAA Security Risk Assessment (SRA) by December 31st – and time is quickly running out. But many private practices and healthcare organizations are not sufficiently prepared to complete their SRA alone. The assessment is lengthy and complex, and most organizations simply do…
How to Be HIPAA Compliant: Is Training Enough?
In the ever-evolving world of healthcare, protecting sensitive patient information isn’t just a good practice—it’s the law. HIPAA has long been the North Star guiding healthcare organizations toward data security and patient privacy, while employee HIPAA training is often the first step taken to ensure compliance. But while HIPAA compliance…
Who’s Completing Your HIPAA SRA This Year? How to Decide
The deadline for submitting your HIPAA security risk assessment (SRA) is getting closer. And the biggest mistake small and medium-sized businesses (SMBs) can make is waiting until the last minute to start thinking about the assessment. Many healthcare organizations, especially small ones, feel heavily burdened by the complexities of the…
5 Things You Need to Know for HIPAA Compliance in 2024
HIPAA compliance is changing. New ways of working in the healthcare industry, the migration to digital, and evolving technologies have driven updates to the HIPAA privacy rule in 2023 that will become fully enforceable in 2024. But it’s not just the official rules that have changed; it’s also the approach to…
3 Strategies for Eliminating HIPAA Location Sampling Risks
Healthcare organizations that have many locations often resort to making the difficult choice of sampling care delivery locations to manage cost and scope when performing their annual HIPAA Security Risk Assessment (SRA). As our previous article on location sampling illustrates, organizations struggle to fully assess all locations due to the…
The Risk of Sampling Care Delivery Locations for Your HIPAA SRA
The HIPAA Security Rule requires that Covered Entities and participating Business Associates perform an annual Security Risk Assessment (SRA) to demonstrate that they are taking steps to safeguard Protected Health Information (PHI). While conducting an SRA is a straightforward idea, how this applies to larger organizations with multiple care delivery…
5 Principles to Keep in Mind When Starting Your Security Risk Assessment
Healthcare organizations in the United States have been the most compromised by data breaches for several years, and that’s not likely to stop anytime soon. That’s why organizations in the healthcare industry, regardless of size, must conduct an annual security risk assessment (SRA) to identify vulnerabilities, remediate risk, prevent dangerous…
7 Reasons Why Your HIPAA SRA Is Taking Too Much Time
Almost all healthcare organizations in the United States – large and small – are required by the Federal Government to complete an annual HIPAA Security Risk Assessment. The purpose is to certify that they are taking adequate steps to protect sensitive patient health information that is in their care. Unfortunately,…
Act Now: The Risks of Postponing Your HIPAA Security Risk Assessment
We’re over halfway through the calendar year– have you started your HIPAA SRA yet? Between the endless day-to-day needs of an organization and complicated HIPAA requirements, many organizations elect to wait until the end of the year to conduct their HIPAA assessment. While it may be tempting to push your…
The Five Best HIPAA Compliance Software Packages
Given how complex and time-consuming HIPAA compliance has become, it’s unsurprising that a growing number of software solutions have hit the market – all promising to make the process smoother, simpler, and more efficient. But which software will serve your organization’s specific needs – and how can you be sure…
10 Things You Should Demand of Your HIPAA Software
HIPAA security and privacy are cornerstones of basic healthcare security practice. Why? Because your organization’s stored protected health information (ePHI) is the single most important vulnerability your company or medical practice has. ePHI is very valuable to hackers, is sometimes easily available to be stolen, and you face significant fines…
Defending Yourself in the Event of an OCR Reportable Breach
Between 2009 and 2021, the Office of Civil Rights (OCR) received 4,419 data breach reports involving 500 or more medical records for healthcare entities. And that number just keeps growing. So, what can you do if you experience the loss of protected health information (PHI) that results in an OCR…
Cybersecurity and Assessments for Hospitals: From 0 to 100
Hospitals and healthcare providers carry a heavy load when it comes to security: not only is patient data among the most sought-after resources for cybercriminals, but it is also among the most heavily regulated areas of cybersecurity. These issues are exacerbated by: Complex digital supply chains: A medium-sized hospital…
How To Improve Your Healthcare Cybersecurity Posture In 2024
Post-COVID cybersecurity has been driven to new heights of threats, costs, awareness, and accountability. With the latest Becker Healthcare press releases regarding breaches, it’s no surprise that cyber-insurance premiums are increasing by 50% or more. Every healthcare organization we speak with has Board-level “cyber” reporting and accountability. What can you…
HITRUST Certification Cost: How to Streamline & Scale the Comprehensive Process
Any healthcare cybersecurity or risk management professional will tell you that HITRUST is the definitive “Gold standard” for compliance and risk mitigation. Why? It stems from thorough, precise methodology combined with a holistic view of verified, implemented controls and organizational processes. There’s simply no substitute in today’s sophisticated, high-stakes era…
Cyber Insurance for Healthcare: Are You Compliant with Your Own Cyber Policy?
Legal fees. OCR fines. Insurance costs. Community embarrassment. When it comes to a cybersecurity breach, the price healthcare organizations have to pay adds up, both literally and figuratively. That’s where cyber insurance for healthcare comes in. Insurance can help cover the steep cost of data breaches; no wonder the cyber…
Cybersecurity Nightmares: The Cost of Healthcare Cyberattacks in 2024
Cyberattacks have always been common in the healthcare industry, but activity has increased sharply in the past few years. Healthcare organizations worldwide averaged 1,463 cyberattacks per week in 2022, up 74% compared with 2021. The average cost of each breach is about $10 million, making healthcare the largest and fastest-growing…
18 HIPAA Identifiers: What They Are & Why Knowing Them Matters
Between 2017 and 2021, complaints about HIPAA violations increased by 39%, and significant breaches reported increased by 58%. There are several reasons why HIPAA violations continue to increase, including covered entities and internal employees not knowing the full extent of the HIPAA Privacy Rule and its mandatory protection of PHI. …
HIPAA Exceptions: What You Need to Know
HIPAA regulations are a major concern for healthcare organizations. But many are so concerned with maintaining compliance that they miss instances when HIPAA rules don’t apply. There is a full page dedicated to HIPAA exceptions in the Administrative Simplification provisions – and understand them is key to an efficient and…
HIPAA 101: What Does HIPAA Mean?
“HIPAA: The federal law many people don’t actually understand.” That’s the telling title of a recent news article, which goes on to state that it’s not spelled “HIPPA” or “HIPPO,” but rather HIPAA, the elusive healthcare-related act that even healthcare professionals sometimes get wrong. Many hear about HIPAA within…
Avoid Phishing Attacks with HIPAA Training for Medical Office Staff
In 2022, 36% of all data breaches involved phishing. Phishing in healthcare has become an increasingly popular tactic for cybercriminals looking to breach databases and collect sensitive health records to sell or hold ransom. What exactly is phishing, why is it so dangerous, and how can HIPAA training for medical…
What Entities and Information Does HIPAA Protect?
An individual’s medical and healthcare records often contain sensitive identifying information that many bad actors would like to get their hands on. It’s no surprise, then, that 95% of identity theft incidents come from stolen healthcare records. Health records have to be protected at all costs, which is why…
Back to the Basics: What is the HIPAA Privacy Rule?
As of November 2022, the Office for Civil Rights (OCR) has settled 126 cases of HIPAA violations for over $133 million. Complying with the HIPAA Privacy Rule is a critical, ever-evolving piece of healthcare and patient privacy. A breach of HIPAA can – and often does – result in costly…
4 Steps to a Successful HIPAA Security Risk Assessment
More healthcare records were exposed in IT or hack incidents last year than any other year in history – and the number of OCR penalties for HIPAA violations was the third-highest ever. But with growing security threats from political actors and AI-driven criminal activity, how can your organization stay safe…
How Small Physician Practices Can Assess HIPAA Security Risks
With the number of possible violations that can land you with fines or even criminal charges, following HIPAA regulations is critical to protecting your patients’ privacy and keeping your practice alive. Constant vigilance and routine security and privacy risk assessments are vital to staying compliant. But what if you are…
4 Key Elements of HIPAA Compliance in Today’s Evolving Environment
HIPAA compliance remains a critical and ever-evolving piece of healthcare and patient privacy. HIPAA (Health Insurance Portability and Accountability Act) protects sensitive patient data and health information, upholding the integrity of medical and healthcare organizations and supporting patient rights. However, with the ongoing and explosive escalation of new technologies like…
405(d) and HIPAA: Roadmapping your Cybersecurity and Compliance Journey
HIPAA compliance is a foundational requirement for any healthcare organization. However, the ever-increasing complexity and frequency of cyber-attacks require healthcare organizations to invest more resources in cybersecurity and risk management strategies to further protect their digital assets and data. The 405(d) HICP security practices were architected by the Department of…
405(d): What is it and why should you care?
What is 405(d)? With security incidents and breaches increasing year over year within the healthcare sector, it is up to both public and private organizations and cybersecurity experts to build a more secure healthcare system. In 2015, congress passed the Cybersecurity Act to help combat the increase in cyber threats…
Keys to Successfully Achieving HIPAA Compliance
Are you looking for some best practices to complete your HIPAA compliance this year? We can help! Here are a few things you can do throughout the year that will go a long way to ensuring security and compliance. Many organizations put off completing their Security Risk Assessment (SRA) until…
Your Guide to Better Cybersecurity and Compliance
Many organizations wonder how to adequately plan for compliance and security tasks throughout the year. Security and privacy challenges are continuing to evolve which means your 2022 roadmap needs to keep up to meet compliance requirements and reduce your risks. This roadmap checklist includes annual, quarterly, and ongoing…
HITRUST i1 Frequently Asked Questions
During a recent webinar we received several questions about the new i1 and r2 HITRUST assessment options. For easy reference, we’ve summarized the questions and answers in this blog post. Q. What was the basis for deciding which controls go into i1? A. HITRUST took several frameworks and industry segments…
So Many HITRUST Offerings: Which Option Is Right For You?
Understanding the nuances of the new HITRUST assessment portfolio can be difficult, especially when trying to determine which assessment is right for you. In this blog we will outline the types of HITRUST assessments, their differences, key characteristics, and possible use cases for each. Starting with the highest level of…
Navigating Your HITRUST Assessment Scope
What is a HITRUST assessment scope and why is it so important? Scoping is the process of outlining the systems and datasets you plan to include in your HITRUST assessment. It is a necessary step in the HITRUST process and should be your first level of engagement with HITRUST. Scoping…
vCoffee Chat | Michaela Iorga – Ep 3: Part 2 – Real-world applications of NIST OSCAL
In Part 2 of this episode with Michaela Iorga, PhD, Senior Technical Lead at NIST and OSCAL Strategic Director, Vikas and Dr. Iorga discuss how the NIST Open Security Controls and Assessment Language (OSCAL) is being utilized in real world settings to automate the risk assessment process. Dr. Iorga describes…

CMS Requirements for MIPS 2022 – What’s at Stake?
Written by Sarah Reiter, SVP Strategic Partnerships with Health eFilings On November 2, 2021, the Centers for Medicare and Medicaid Services (CMS) issued the Final Rule for the 2022 MIPS program. These rules detail the requirements for this MIPS reporting period, which started on Jan. 1, 2022, and align with…

Intraprise Health’s NIST Assessment Platform
The Intraprise Health NIST Assessment Platform was designed to help organizations adopt the NIST Framework and identify and prioritize cybersecurity risks. The NIST Cybersecurity Framework provides organizations with a “common language” to measure security risks and a clear way to communicate compliance to internal and external stakeholders. Build a comprehensive…
vCoffee Chat | Michaela Iorga – Ep 3: Part 1 – What is NIST OSCAL?
In this coffee chat, Michaela Iorga PhD, Senior Technical Lead at NIST and OSCAL Strategic Director, provides an overview of NIST’s Open Security Controls Assessment Language (OSCAL). OSCAL is a true innovation which has the promise of transforming the risk assessment process. Michaela discusses why NIST launched the project, provides…
How to Quickly Address Your HIPAA Compliance Issues
Let’s be honest, if you are reading this, you probably still have “complete your HIPAA Security Risk Assessment (SRA)” on your to-do list and you are wondering what you can do to get it done before the end of the year. (December 31st is right around the corner) We understand procrastination, but we also understand the importance…
Cloud-Based HIPAA Security Risk Assessment Software
Many organizations use time-consuming and inaccurate manual processes for compliance, such as complicated spreadsheets and uninspired templates. Simple, automated, and affordable, our software focuses on efficiency as well as accuracy, helping remove the administrative burden of compliance. Watch the short video below to learn more. Take the confusion out of…
Addressing HIPAA Privacy Rules and Cybersecurity for Hospitals and Health Systems
Managing HIPAA compliance can be a messy, complex process; especially for hospitals and health systems managing compliance for hundreds of individual clinics and practices. It can be difficult to track, maintain and report on risk management and cybersecurity efforts. Many organizations are using time-consuming manual processes such as spreadsheets and emails for compliance, which can require a significant investment of time,…
The Simplest Way to Manage Your Business Associate Agreements
Importance of a Business Associate Agreement The Privacy Rule under HIPAA requires the safeguarding of protected health information (PHI) and applies to all covered entities (CE) – healthcare providers, health plans and healthcare clearinghouses. Most providers do not carry out ALL their necessary healthcare functions. Billing, medical software, and electronic…
vCoffee Chat | Serge Loncar – Ep 2: Part 2 – Tech Innovations in Home Health and Elderly Care
In part two of this discussion, serial entrepreneur and innovator Serge Loncar shares the latest trends and uses of tech in the home health setting with a specific focus on elderly care. Learn about the use of sensors that enable “smart” fabrics, mirrors and door knobs. Serge describes how these…
Essential Tips for HIPAA Security, Privacy, & Breach Compliance
HIPAA compliance can be difficult to approach on your own. Healthcare providers and their business associates are required to perform an annual HIPAA Security Risk Assessment (SRA) to ensure that proper physical, administrative, and technical controls are in place to protect health information. By performing a security risk assessment, not…
Implementing cybersecurity measures BEFORE you experience a breach
A cybersecurity nightmare “IT just informed us that our main software platform has been hacked.” A statement no CISO wants to hear. Do you have a plan for what to do next? Are you prepared to handle this? How will you recover servers and client data? As an organization, are…
Remote Cybersecurity: Best Practices
Remote work is here to stay Many of us have been working remote for over a year now. The pandemic hit in March of last year and virtually all industries had to adapt. The transition was sudden at the time, and IT and security personnel quickly had to organize their workforce to successfully work remotely. Work from Home (WFH) is no longer a temporary solution…
HIPAA Compliance in the Changing World of Healthcare
A Changing World of Health Care The health care and HIPAA landscape have changed dramatically since the beginning of 2020. Reliance on telehealth and telecommuting has put practices at further risk for security breaches. Cyber Threats (Ransomware, Email Phishing, etc.) are increasing and becoming more successful. These are just a…
Elevating Your Privacy Compliance
Proposed changes to the HIPAA Privacy Rule are expected to be finalized in late 2022, with compliance enforcement likely beginning in 2023. These changes reflect the health care industry’s increased use of mobile communication, telehealth platforms and electronic health records, as well as updates to right to access requirements that…
The History of HIPAA and HITECH: Everything You Need to Know
The Establishment of HIPAA The Health Insurance Portability and Accountability Act, also known as HIPAA, was established on August 21, 1996. HIPAA was created to promote the portability and accountability of health insurance coverage. Consequently, it has affected the way healthcare organizations handle all facets of information management, including reimbursement,…
vCoffee Chat | Serge Loncar – Ep 2: Part 1 – Navigating Security, Privacy & Compliance to Innovate
Healthcare, specifically the health system, health plan and life sciences sectors are market segments that pose significant regulatory and risk management challenges for companies trying to innovate in this space. In this discussion, serial entrepreneur Serge Loncar shares real-world insights about tough lessons learned about investing early on in security,…
vCoffee Chat | Hector Rodriguez – Ep 1: Part 3 – Ransomware Prevention Strategies
With the industry suffering from severe and constant ransomware attacks, Hector and Vikas talk about strategies that security leaders can take from holistic and complete approaches, real-time threat alerting, new emerging, highly-scalable cloud-based security training solutions to the need for a Chief Ransomware Strategist/Officer. Disclaimer: The content in this chat…
vCoffee Chat | Hector Rodriguez – Ep 1: Part 2 – Blockchain and Crypto Use Cases in Healthcare
In this episode, Vikas and Hector explore emerging uses of blockchain and crypto in healthcare. Several use cases are explored from global COVID vaccine distribution, medication management and adherence, medical device IoT implants to democratizing data for healthcare consumers and providers. Learn about Merkel trees and other aspects of the…
vCoffee Chat | Hector Rodriguez – Ep 1: Part 1 – Introduction & Scalable Threat Management
Vikas welcomes Hector and learns about his spirit animal before discussing the latest threat management trends focusing on SIEM, SOAR and XDR. What’s the difference between these acronyms? How should these solutions be implemented? What does the future of automated threat intelligence look like? They also discuss how leading threat…
NIST RMF: The “Prepare Step” of Implementation
The NIST RMF is increasingly being seen as the gold standard for industries with critical or highly sensitive data needs – such as healthcare. It is an effective security planning and management framework that enables a comprehensive picture of organizational risk. This helps organizations build a solid risk management strategy, understand the areas that matter most to their organizational security and enable them to properly perform their essential business functions. NIST RMF:…
How to Choose HIPAA Security, Privacy, and Compliance Officers for Your Compliance Program
Few areas cause more headaches for healthcare leaders than HIPAA compliance. With the prospect of seven-figure fines for a serious violation, adhering to these regulations is a major priority – and that requires a strong compliance team. But the terms privacy officer, security officer, and compliance officer are all used…
HIPAA Violations: Who Enforces Them & How to Avoid Them
The Health and Human Services, Office for Civil Rights (OCR) is the governing body that enforces HIPAA and the consequences of HIPAA non-compliance. Periodically, the OCR will send out updates and announcements of recent HIPAA infractions. These announcements typically outline the HIPAA violation, the fine associated, and what corrective action…

Military service to country provides Intraprise Health staff with lifelong memories and skills
Serving our country is meaningful for Intraprise Health, especially for those employees who have served in the U.S. military. As a healthcare focused IT security firm, located in Yardley, Pennsylvania, Intraprise Health relies on its strong core of veterans to navigate the ever-changing cybersecurity landscape. Read full article
New State order for Health Insurance Companies
Insurance Data Security Risk Assessment and Reporting The state of Virginia announced this week that they have made changes to state HIPAA laws (14VAC5-430) and are now formally requiring health insurers to perform an annual NIST-based Cybersecurity Risk Assessment. The new requirements were released in a statement from the Commonwealth of…
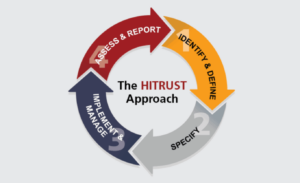
What Is HITRUST Certification and Why Do You Need It?
A recent report showed that healthcare is the biggest target for cyberattacks globally. But with large vendor networks, increasingly complex IT systems and a range of regulations to contend with – under HIPAA, Meaningful Use, PCI, COBIT and ISO – the sector struggles to manage these risks. That is why…
We can help you access the LADMF
What is the LADMF? Healthcare organizations must access the LADMF to keep records up to date and prevent fraud. LADMF stands for Limited Access Death Master File, it is a database maintained by the Social Security Administration and contains over 86 million records on deceased individuals. This online file has many…
Understanding & Complying with HIPAA: Know Your Risks
HIPAA laws can be complex and challenging, but they are also increasingly critical for healthcare practices to understand and be in compliance. As more of your practice becomes digital in one form or another—electronic health records (EHRs), remote patient monitoring, practice management systems, medical billing software—your risk of a breach…
I have experienced a breach, now what?
What should I do? Navigating the world of HIPAA can be difficult; and in the event of discovering a breach, many are unsure of how to proceed. According to the Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR), “a breach is an impermissible use or disclosure…
Fast and Easy Online HIPAA Training & Certification
Need to complete your annual HIPAA training? Get started today with the HIPAA One® Knowledge Center! HIPAA One® Training Platform HIPAA training is an important element of any HIPAA compliance program. At Intraprise Health, our goal is to provide a training solution that simplifies the HIPAA compliance and certification process. As…
HIPAA One® Summer Release 2020
Intraprise Health is excited to announce the new features and updates for our HIPAA One® Summer Release 2020. The updates added to the HIPAA One® platform are designed to enhance the user experience through easier navigation, simplified workflows, and customized reporting. As an industry-leader for HIPAA compliance, our goal is…
The Protection of ePHI in the Face of Telehealth and COVID-19
What is Telehealth? The Health Resources Services Administration (HRSA) defines telehealth as, “the use of electronic information and telecommunications technologies to support long-distance clinical health care, patient and professional health-related education, public health, and health administration. Technologies include videoconferencing, the internet, store-and-forward imaging, streaming media, and terrestrial and wireless communications.”…

HITRUST Assessments: Relying on the work of others
HITRUST has been a trusted framework since it was founded in 2007. It was created to champion programs that safeguard sensitive information and manage information risk. Intraprise Health is one of the first certified HITRUST assessors and is 100% healthcare focused. We know the importance of ensuring organizations are secure…
Microsoft Office and HIPPA Business Associate Agreements
Note: This information has been updated, please visit our Microsoft Office 365 page. Health and Human Services (HHS) defines a Business Associate as, “any entity or person that is not directly employed by a provider, but who works with and on behalf of the provider and has access of the…

Healthcare Payers: Scalability and Risk Management-Based Prioritization
As healthcare payers surge to meet the increasing needs of their members and health system partners, their IT and security teams are gleaning some timely reminders that scalability and adoption of a risk management framework are critically important in times of crisis. What is Scalability in Healthcare? Scalability is a…

Focused Security Risk Assessments: Remote Work for Healthcare Organizations in the Age of COVID-19
May 2020 As the reality of working from home sinks in, many remote workers and their employers are seeing the appeal fade quickly. We all know that remote work is not quite as simple as it sounds. Technical, operational, and communication challenges are quickly presenting themselves when workforce members overload…
Staying Alert: Coronavirus-themed phishing emails on the rise
COVID-19 phishing emails: The second virus you didn’t see coming As the Coronavirus spreads around the world, much of the workforce has been invited to work remotely for the next few weeks. It is important to uphold current security measures as well as implement new security measures to ensure the…
Coronavirus and HIPAA Compliance
During a public health emergency, it can be confusing to know what information can be shared about individuals who have contracted COVID-19 and those suspected of exposure. To help organizations navigate the complexities of sharing information, we want to walk through what disclosures are permitted. Before we jump in, it…

Resources for Healthcare Organizations During COVID-19 Pandemic
As COVID-19 changes the way many healthcare organizations are operating, Intraprise Health has been compiling a list of resources that we think will be useful to your organization. Our team of cybersecurity experts has been fielding questions from clients on many of these topics. Links to resources such as securing your work from home force, to…
Developing a HIPAA Contingency Plan in the Shadow of COVID-19
We’ve received several inquiries from our colleagues in the healthcare industry related to the increased prevalence of remote work and contingency operations. Given these uncertain times, we wanted to share a few thoughts that might help as we proceed into some new and uncomfortable realities. Business as Usual (As Much…
HIPAA Compliance Resources for COVID-19
With the recent Coronavirus outbreak, many healthcare professionals and business associates have questions about staying HIPAA compliant during a public health emergency. It can be confusing to know what information to trust. We have complied a list below of trusted sources for COVID-19 updates and HIPAA. COVID-19 Resources: CDC.gov/coronavirus…

What is a Penetration Test & How Do You Request One?
As we continue to rely on the interoperability of our computer systems in our everyday lives, we must remember this interconnectivity comes with a price. The ability to access devices remotely over the internet has created a new world of ease and freedom which can be manipulated by malicious actors. It’s quite eye-opening in its simplicity: If a device is…
Lessons learned from a $65,000 HIPAA fine
Last week the Department of Health and Human Services’ Office for Civil Rights (OCR) issued a press release announcing that West Georgia Ambulance has agreed to pay a settlement of $65,000. In addition to the monetary penalty, the organization agreed to adopt a corrective action plan that includes two years of monitoring…
The Present (and Future) of Healthcare IT Security
It has been another busy year for Healthcare IT. Between acquisitions, changes in regulations, and IoT, there has been a lot of progress. However, there is one trend we aren’t so proud of and that is the number of breaches that have happened in 2019. If you made it to…
HIPAA Enforcement is Here to Stay
Even though Meaningful Use, now MIPS, has been in production since 2012, often, we hear healthcare providers tell us they haven’t started their HIPAA compliance because they are too small to worry about being audited. Some also claim that the Office of Civil Rights (OCR) has eased their enforcement of…
Top HIPAA Compliance Pitfalls to Avoid
If you work in the healthcare industry, you have heard the term HIPAA. Many healthcare professionals understand the basics of HIPAA, but few know what is required to fulfill HIPAA requirements and to be “HIPAA compliant.” This is especially concerning because organizations that don’t understand are neglecting to prioritize their…
Substance Abuse and HIPAA
War on Drugs It was the 1970’s: a time of disco dancing, polyester suits, and crazy nights. It was also time of increasing stress, depression, and anxiety following the Vietnam war and Watergate scandal. Many people were looking for an escape and turned to alcohol and drugs. This new era,…
Raising the standard of cybersecurity
New cybersecurity questions have been added to the HIPAA One™ Security Risk Assessment. Cyberattacks on healthcare organizations are continuing to rise and the threat of a breach is a top concern for many organizations. Each time we turn on the news there is a new report of a ransomware attack…
Third-Party Risk Management: Keeping Your Healthcare Organization’s Information Safe
Read the latest article by Intraprise Health’s CEO, Sean Friel in Security Magazine. “As the person in charge of your healthcare organization’s information technology, one of your responsibilities is protecting patients’ and clients’ information. This can be difficult because third-party vendors with whom you contract can unwittingly jeopardize the security…
Why it might be time to ditch SMS for MFA
BLUF: multi-factor authentication (MFA) utilizing SMS (i.e. text messaging) leaves an organization open to vulnerabilities. IT departments, users, and platform operators should cease use in lieu of vastly more secure app-based or hardware options. If you are serious about security, it is time to think twice about using text-messaging (SMS)…
Mitigating the Risks of Ransomware Attacks
It’s no secret that organizations across the world in nearly all verticals have been reeling from the destructive effects of ransomware over the past several years. News outlets have been flooded with tales of lost productivity, revenue, and exorbitant sums paid. And from our experience, a substantial majority of these…

What to Know About Split Tunneling
Today’s modern networks require flexibility to allow workers to work from multiple locations. One of the most common methods to achieve remote network access is a Virtual Private Network (VPN). VPN’s can come in all shapes and sizes, from hosted to on-premises, to in the cloud, and can be built…
Security is a necessity, NOT a luxury
I recently read a story about a man who won the lottery. Unlike most, this man opted for an annuity payment rather than the lump sum payment. This resulted in a smaller yet substantial sum of money being awarded annually over a twenty-year period. As time went on, the man…
Intraprise Health platform strengthens healthcare security
Intraprise Health introduced new software designed to prevent healthcare security breaches by monitoring third-party risks across the enterprise and improving security management processes. To help healthcare organizations manage and automate security programs, Intraprise Health introduced BluePrint Protect Security Risk Management Software. The software service intends to provide users with a…
Intraprise Health BluePrint Protect can help detect, manage security risks
BluePrint’s visualization software coalesces security program data from disparate sources into a central “source of truth” founded on the company’s workflow automation and rules engine. Intraprise Health BluePrint Protect can help detect, manage security risks BluePoint coalesces security program data from disparate sources into a central “source of truth” founded…
Ransomware: 3 ways to protect your organization
News Update: healthcare organizations are being hacked 24/7. Those experiencing a ransomware attack can feel similar to having your home burglarized. In many cases, targeted hacking is financially motivated to hold data hostage and make payroll. Hackers target executives because they have a lot of access to secured information. With…

How to Prepare for HITRUST Certification: Gaining Organizational Support
Why HITRUST? More than 81 % of U.S. hospitals and health systems and 80 % of U.S. health plans use the HITRUST Common Security Framework (CSF). It provides an implementation standard that is understood and accepted throughout the healthcare industry. Having HITRUST certification in place shows other healthcare entities that…

Zero Trust Architecture and the Future of Networking
By Joshua Perri In today’s networks, having a strong defense at the perimeter-points is not sufficient to keep your data safe. The IT landscape moves very quickly and so do the threats that we face. Strong networks will implement additional defenses to protect the internal boundary points. These additional defenses…
A Balance of Trust: New Guidelines for Business Associates Under HIPAA
The relationship between a covered entity and business associate requires a delicate balance of trust. This balance of trust works because each is invested in the security and protection of personal health information. As a covered entity, it is important to partner with business associates that have a strong security…
Don’t get caught! Five ways to avoid a phishing scam
I love to spend time with my family. Some of our favorite outdoor activities include skiing and mountain biking. Unfortunately, this time of year it is hard to do either activity because the snow is too slushy to ski and the canyon trails are too muddy to mountain bike. However,…

Tabletop Exercises in Cybersecurity: Unappreciated and Underutilized
Not Just a Government Tool: Tabletop Execise’s Value for Cybersecurity Government defense and response agencies from the Pentagon to FEMA, from state government to the EPA, have been conducting tabletop exercises (TTXs) for years. Why? In a word: they work. Cybersecurity attacks have been increasing in numbers and complexity against…
4 Tips to Help You Protect Your Medical Devices
How do you best protect your hospital or health system from the unique threats posed by unprotected medical devices? We asked our expert Ryan Patrick, for some tips.
DV-NJ HIMSS Post-Conference Blog
Inspira Health Network: Using CRM to Create an Engagement Ecosystem
Patient Engagement Platform at Inspira Health Network
Health network uses Dynamics 365 to transform care delivery and wow patients July 13, 2018 In a market where every provider delivers quality, Inspira Health Network wanted to go one step further by offering wow-factor patient service. So, the New Jersey–based healthcare provider adopted Microsoft Dynamics 365 to deepen its…
Inspira Health Network: Using CRM to Create an Engagement Ecosystem
By Jeff Fisher Product and Client Strategy, Intraprise Health In 2016, Inspira Health Network came to Intraprise with a goal: “Wow the patient.” As reimbursement models shift and healthcare is becoming more consumerized, forward-thinking health systems like Inspira are seeking new market differentiators to draw in clients.

Four Tips to Help Protect your Medical Devices
The Challenge of Medical Devices: Medical devices represent significant exposure and potential vulnerability to healthcare organizations. There are thousands of medical devices in use even in small medical operations. These devices are generally made to meet a specific use, and not often created with security at top of mind. They…

POODLE and the BEAST: Ensuring you’re protected with Transport Layer Security
Transport Layer Security (TLS), and its predecessor Secure Sockets Layer (SSL), have come under scrutiny by security researchers and advisors in the wake of numerous vulnerabilities that plague their older versions. SSL/TLS are cryptographic protocols utilized while web browsing, emailing, and using Voice Over IP (VOIP) services.

Take a fresh look at your annual Security Risk Assessment (SRA)
Organizational Resilience and Security Risk Assessments The importance of a Security Risk Assessment is clear — it helps healthcare organizations ensure their physical, technical, and administrative safeguards are compliant with HIPAA requirements. It also assists in showing areas where an organization might be putting PHI and other sensitive information at…
Am I a Business Associate Under HIPAA? Why Should I Care?
Back in 2013, when Edward Snowden was in Hong Kong revealing he leaked documents detailing mass-surveillance programs by the U.S. government, the Department of Health and Human Services (HHS) was creating the Final Omnibus Rule. This rule extended its regulatory reach beyond covered entities (e.g. healthcare providers, health plans, and clearinghouses)…
Configuring Microsoft Office 365 for HIPAA Compliance
Organizations in every industry are upgrading to Microsoft Office 365 to improve security. A common concern among healthcare professionals is that using Office 365 and Microsoft Teams exposes an organization to HIPAA violations. If Office 365 is implemented without the correct security configurations, that is likely true. However, Office 365…
HIPAA Security Checklist
Our complimentary HIPAA Security Checklist summarizes HIPAA Security Rule requirements that should be implemented by covered entities and business associates. The citations are to 45 CFR § 164.300 et seq. You can download our checklist here. For additional resources concerning Security Rule requirements and compliance assistance, see the Office for Civil Rights (OCR)…
Healthcare Continues to Dominate Breach Related Costs
Across the country, healthcare organizations have a Goliath size security problem. For an eight-straight year, healthcare has the highest breach-related costs of any industry at $408 per lost or stolen record, nearly three times the cross-industry average of $148. Without a commitment to cyber-security, healthcare entities and their valuable databases containing…
Similar But Different: HIPAA Gap Assessment vs. Risk Assessment
If you’ve heard the terms gap assessment and risk assessment used interchangeably before in privacy or security conversations, you are not alone. At Intraprise Health, we have found that there are quite a few misconceptions about these two approaches and how to differentiate between them. In this post, we’ll define…
Windows 10 and GDRP vs. HIPAA Compliance
Note: This information has been updated. Please visit our M365 Compliance page. On April 14, 2016, the European Union (EU) ratified the final version of the General Data Protection Regulation aka GDPR. The new GDPR regulation has been characterized as the most sweeping and impactful change to privacy and data…
GDPR and the Impact on U.S. Healthcare Providers
A new acronym has begun popping up within the healthcare technology community and is slowly beginning to gain momentum in the way of media coverage and industry articles. If you’ve heard the term GDPR in the past few months and did not understand what it was referring to, know that you’re not alone. In fact,…
Cloud Security in Healthcare
Guest Blog by Yiannis Koukouras, TwelveSec in collaboration with the HIPAA One/Intraprise Health team In our culture, something or someone is always trending. Whether it be bell-bottom jeans in the ’70’s, playing Nintendo in the ’80’s or watching stock market go up and down (whenever!), trends are a lenses through…
What Happens if you Break HIPAA Rules: Violation Consequences of Non-Compliance
HIPAA compliance is not just a legal requirement – it is essential to protect your patients, reputation, and financial health. Non-compliance can lead to $16 million fines, with penalties extending to jail time in some cases. But given that HIPAA is treated differently within covered entities, business associates, and the…
We’ve Helped Many Access the LADMF! Need Assistance?
Note: This information has been updated. To see the latest updates, read our most recent blog. Last May, we wrote a “How To” blog on the Social Security Limited Access Death Master File (LADMF) aka DMF and the response has been overwhelming! The Intraprise Health team is delighted by how…
Newly Released Whitepaper Co-Authored with Microsoft
We updated our Microsoft Whitepaper in November of 2021. For more recent information on the subject, click here. The concept of the “Internet of Things” (IoT) is becoming an increasingly growing topic of conversation as more and more companies are interconnecting everyday objects around us to the internet, such as:…
PCI vs. HIPAA Compliance
A common question among covered entities that we encounter time and time again is, “What is the difference between PCI and HIPAA Compliance?” This question becomes even more frequent when news breaks of breaches in businesses that are PCI-compliant and HIPAA covered entities. According to a recent Identity Theft Resource Center data…
Need to Access the LADMF? We can help
Note: This information has been updated. You can read our latest LADMF blog here. In the world of HIPAA compliance, sometimes the only constant is change. It is not out of the norm for one of our clients to come to us with a question or request that at times,…
What is HR’s Role in HIPAA Compliance?
In recent years, many healthcare organizations have faced the same question: Which department should be tasked with Health Insurance Portability and Accountability Act (HIPAA) compliance? More times than not, the finger points to IT. However, in doing so, organizations are overlooking the key component Human Resources (HR) should play in…
OCR HIPAA Audit Program: What You Need to Know
Healthcare cybersecurity has never been under more scrutiny – or more in need of improvement. The volume of data breaches has more than doubled since 2017, with more than $6 million in HIPAA fines from the Office for Civil Rights (OCR) in 2024 alone – all of which help explain…
7 Ways Employees Can Help Prevent HIPAA Violations
Every healthcare employee understands the importance of data privacy; a single person’s actions can jeopardize the entire organization. But let’s be honest: the HIPAA Privacy Rule or Security Rules are extremely complicated. So how you actually protect patient health information in the workplace? This article explores seven clear and actionable…
Dental HIPAA Compliance: What You Should Know
Today, most dental offices run electronically. From having patients fill out forms to checking them in to appointments to filing dental records and more, it’s all done electronically. Why? Because the advancements of technology allow dentists to run their offices more efficiently than ever before. But since we live in…
The Most Common HIPAA Violations: A Guide for Healthcare Leaders
American healthcare organizations spend up to $120,000 every year on HIPAA compliance. But many leaders worry they are not focusing that budget on the right factors – and therefore may end up with a costly HIPAA violation. What are the most common ways healthcare organizations violate these rules? What are…
Key Differences of Covered Entity vs. Business Associate
Knowing the distinction between a covered entity and a business associate is essential because the Health Insurance Portability and Accountability Act Privacy Rule (HIPAA) is administered differently between the two. By knowing the distinction, Compliance Officers and staff can better understand the Office of Civil Rights’ (OCR) expectations of their…
