Mastering Risk Management in Healthcare: Strategies for Success
Posted on: October 2nd, 2024 01:29 pm
Updated on: October 3rd, 2024 04:17 pm

Every healthcare organization understands the importance of reducing risk to protect its patients, reputation, and bottom line. However, putting risk management theories into practice is challenging for most organizations – and that leaves them vulnerable to a range of threats.
This article provides a complete overview to help you select the most effective strategies to manage cyber risks at your organization.
What is Risk Management?
Risk management is a systematic process designed to identify, analyze, manage, and mitigate risks to an organization. These risks cover a wide range of areas, from financial and regulatory threats to events that could disrupt daily operations.
Importance of Risk Management in Healthcare Organizations
While most industries place a heavy emphasis on risk management, healthcare faces more acute risk than most for two primary reasons:
- Patient safety: Disruptions to healthcare organizations can lead to compromised care for patients, with the potential for serious consequences such as missed diagnoses, delayed surgery, and even avoidable death.
- Heightened cyber threats: The healthcare industry also faces unusually high levels of cybercrime due to the value of protected health information (PHI). Cybercriminals attempt to infiltrate organizations in a range of ways, creating numerous forms of ongoing risk.
The net result? Risk management in healthcare is more urgent and has far greater consequences than other industries.
How Does Healthcare Risk Management Work?
Healthcare risk management involves specialized “risk managers” responsible for many activities related to risk management. From creating risk policies and undertaking assessments to overseeing remediation efforts that reduce organizational risk, risk managers collaborate with a wide range of departments to meet their objectives.
Key Objectives of Risk Management in Healthcare
Healthcare risk managers are expected to meet a wide range of objectives, including:
- Protect Patients: Maintain operations to enable efficient delivery of services and patient care.
- Ensure Compliance: Understand regulatory requirements and put measures in place to ensure they are met.
- Assess Technology: Monitor the IT environment to minimize security risks.
- Manage Reputation: Protect the organization from events that would negatively impact its public perception or make it difficult to acquire new patients.
- Reduce Liability: Ensure the organization is aware of and manages its financial and legal responsibilities around cybersecurity.
These objectives cover a wide range of areas, but the risk management discipline increasingly focuses on cybersecurity. As the industry adopts more digital technology, data security and cybercrime have become the most urgent threats to healthcare organizations – presenting a wide range of risks.
Six Types of Risks Healthcare Organizations Face
There are six primary forms of risk in the healthcare industry:
1. Operational Risk
Operational risk refers to the possibility of events that would disrupt daily operations. For example, a lack of personal protective equipment (PPE) or hospital beds could force a hospital to turn patients away or even pause operations while the problem is dealt with. An organization that was close to capacity and did not have a reserve of equipment would be considered to have high operational risk.
2. Patient Safety Risk
Patient safety risk refers to any event or process that could put patients in danger. These are wide-ranging in healthcare, from medication errors to cybersecurity attacks that disrupt care. Healthcare organizations must prioritize any risk that threatens patient safety over other threats.
3. Financial Risk
A financial risk is any potential event that would negatively impact an organization’s financial health. For example, a sudden exodus of patients could significantly reduce the organization’s revenue and lead to extended financial instability. Such risks are often exacerbated by slim operating margins, a lack of financial reserves, or being locked into high-cost contracts with suppliers.
4. Reputational Risk
Reputational risk refers to events that could negatively impact the public perception of a healthcare organization. For example, a large data breach could lead a provider to be listed on the Department of Health and Human Services (HHS) ‘s “Wall of Shame.” This can significantly impact the organization’s ability to acquire new patients or hire staff in the future.
5. Regulatory Risk
A regulatory risk refers to any element within an organization that could lead to non-compliance with regulations. For example, poor employee education could lead staff to access patient data they are not authorized to see, leading to a HIPAA violation. A lack of employee training would, therefore, be considered a regulatory risk.
6. Technology Risk
Technology risk refers to any aspect of the organization’s IT system that could cause problems. This ranges from cybersecurity vulnerabilities that allow malicious actors to access PHI to outdated technology that may stop working or produce sub-optimal performance. 
All Risks are Linked in Healthcare
Of course, these “types” of risk are rarely isolated, as is perfectly illustrated by the recent ransomware attack on Ascension. The attack was caused by an employee accidentally downloading an infected file, which led to the electronic health records (EHRs) being unavailable for 36 days. This created significant problems for providers, with many patient appointments canceled or delayed, as well as nationwide news coverage and ongoing lawsuits.
For providers affected by the attack, this could be reasonably categorized under almost every type of risk covered above. It impacted the organizations’ daily operations, patient safety, financial health, reputation, and technology stack.
This is why we believe healthcare risk managers should approach risk from a holistic perspective – and use established frameworks to understand how these different factors interrelate.
Risk Analysis in Healthcare: How to Identify Risks
There are three popular ways to analyze the full range of healthcare risks:
1. The Bowtie Method
The Bowtie Method enables healthcare risk managers to clearly visualize how risks are managed by showing the relationship between the threats, the potential incident, and the consequences, along with the controls in place to prevent or mitigate the impact of the risk. It is illustrated using the following format:
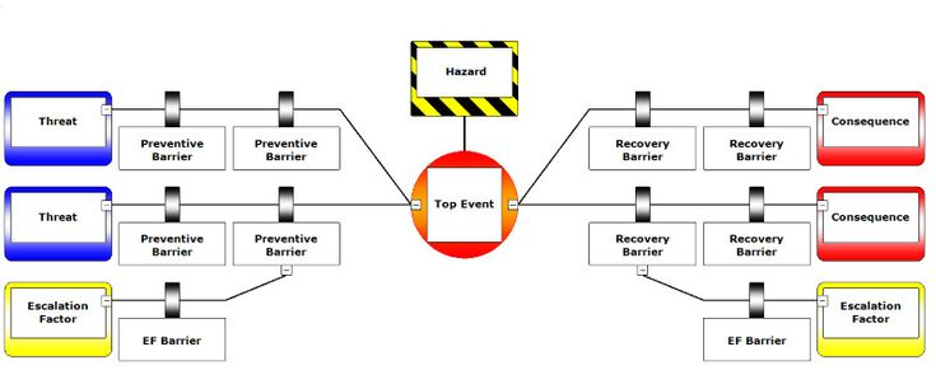
[Source: Wolter Skluwer]
For healthcare risk managers, this offers a powerful framework to understand how a given risk will affect a complex organizational structure. However, it only allows you to analyze a single risk at a time. This can make it difficult to compare risks and prioritize which threats should be dealt with first.
2. Failure Models and Effects Analysis (FMEA)
The failure models and effects analysis (FMEA) model offers a more effective method to understand how different risks interrelate. It has two basic steps:
- Failure Models: Identify the ways in which a system might fail
- Effect Analysis: Assess how these failures would impact the system
For example, a healthcare risk manager might assess the potential for their organization’s IT system to be disrupted. They would first identify all known external threats and identify vulnerabilities within their system before estimating the likely damage each threat would cause.
This helps to compare the true “risk” associated with each threat identified. While an outdated piece of software might pose a small operational risk, phishing attacks could lead to system-wide outages – which helps you focus resources on minimizing overall risk.
3. The Risk Matrix Method
The Risk Matrix Method follows a similar approach to the FMEA model but provides an easy visualization to help risk managers plot their risk. It assesses potential risks based on the following:
- The likelihood that an event will occur
- The expected harm the risk will cause
These two factors are then mapped out as follows:
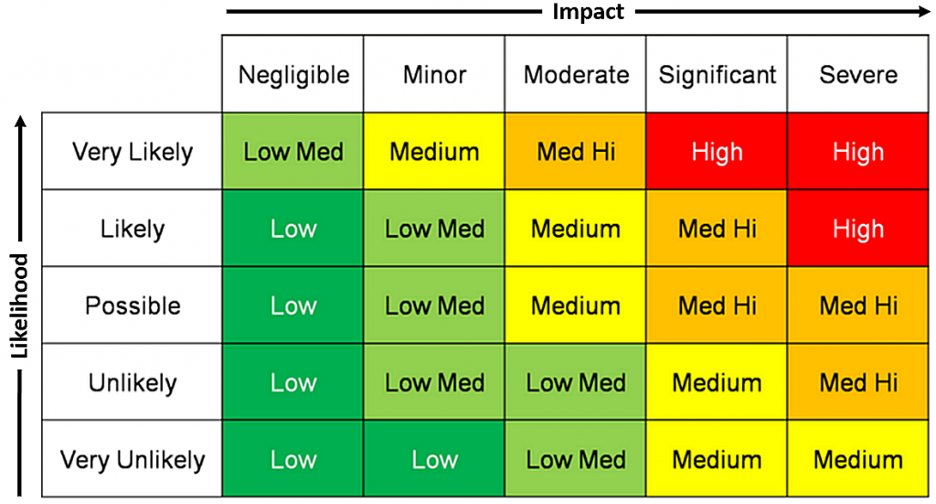
[Source: Dane Boers]
This helps quickly identify the factors that are most urgent across a wide range of risk types.
Response Strategies in Risk Management
Once you have identified which risks are most urgent, there are several approaches a risk manager can take:
1. Mitigation Strategies
Many healthcare risks can be effectively dealt with through the correct mitigation strategies. These aim to reduce the likelihood that an event will occur by dealing with the underlying causes that make an organization susceptible to the risk.
A few examples include:
- Staff Training: Providing healthcare employees with cybersecurity and HIPAA education can dramatically reduce the risk of them falling victim to phishing emails or mishandling PHI.
- Updating Legacy Technology: From upgrading software to implementing encryption on employee communications, there are a range of steps healthcare organizations can take to significantly mitigate the risk that their IT system will be infiltrated by cybercriminals.
- Multi-Factor Authentication: Requiring users to complete a more rigorous authentication process to access data significantly reduces the risk an unauthorized individual will handle patient data.
2. Transfer and Sharing Strategies
Healthcare risk managers should also take steps to limit their liability in the event of a damaging event. These are often known as “risk transfers” or “risk sharing” strategies, as they essentially involve offloading some of the risk to other stakeholders.
A simple example is step-loss insurance, wherein an insurer agrees to absorb financial risks beyond a certain threshold. While this can provide protection for an organization, they are generally a band-aid solution that has limited impact – and can be extremely expensive.
3. Acceptance and Tolerance Strategies
Given the limited resources most healthcare organizations have at their disposal to deal with mounting cybersecurity threats, many opt for a risk acceptance policy. This means they determine that the cost of tackling the risk is not justified by its potential impact. For example, a poor user interface might create operational risk by increasing the likelihood of an employee error, but the organization may decide that changing the software outweighs the potential threat.
The extent to which an organization is willing to opt for this risk acceptance is referred to as its risk tolerance. High-risk tolerance is generally very dangerous in the healthcare industry, as it can lead organizations to offer inadequate protection to their patients.
3. Avoidance Strategies
While most healthcare risks are persistent and must be managed rather than eliminated, there are threats that can be completely nullified. The process of removing risks completely is known as risk avoidance.
A simple example is removing an outdated medical device from the IT system. Many organizations leave old devices connected to their network, which creates a “back door” that cybercriminals can easily exploit. However, discontinuing and disposing of the device eliminates this specific risk.
Ultimately, each of these strategies has its merits. The most important factor for healthcare organizations is not the specific method they use to manage risk – it is that they do it proactively. Whether you want to mitigate, avoid, or share risk, it must be done before an attack occurs – which is why so many organizations require expert support.
Elevate Your Risk Management Program with Intraprise Health
There are two realities most healthcare risk managers must face:
- Risk management is never “complete”
- Protecting your organization is time-consuming and expensive
That is why Intraprise Health exists: our suite of innovative software and guided software helps healthcare organizations adopt risk management best practices without blowing their budget. Whether you struggle with staffing shortages or assessment fatigue, we deliver tailored solutions to ensure your patients, reputation, and bottom line stay safe.
Want to explore how we could help reduce risk at your organization?