
The Complete Guide to HIPAA Compliance
What is HIPAA?
Google that question and you’ll be met with nearly 150 million results in less than half a second.
HIPAA is complex, to say the least. It has seemingly endless moving pieces, a unique associated vocabulary, and impacts a wide array of people and organizations, some of whom don’t even know it.
Plus, since its original inception, HIPAA has drastically evolved to cover newer dangers, like cybersecurity threats. Its ever-changing nature makes HIPAA a hard concept to pin down.
If you’re a healthcare organization (such as a doctor or dental practice, nursing home, psychologist or physical therapist practice, etc.) or a contractor doing business with a healthcare organization, you might see HIPAA as a painful regulation, a series of complicated boxes you must check annually to remain compliant and avoid government intervention. But HIPAA is so much more than that.
We’ve combined our decades of compliance experience and the top questions from over 64,000 healthcare clients to produce this authoritative guide to HIPAA compliance.
You’ll learn everything you need to know about this elusive regulation and gain the tools you need to see HIPAA as an asset and to leverage its framework to help protect your organization and its sensitive patient data.
Read on for all things HIPAA, from the very basics to how to go beyond checking boxes to create a culture of compliance that will safeguard you from cyber threats, data breaches, and irreparable damage.
HIPAA 101: What It Is & Who It Applies To
What Is HIPAA?
What Does HIPAA Stand For?
The acronym HIPAA refers to the Health Insurance Portability and Accountability Act (HIPAA) of 1996. HIPAA is most commonly associated with national standards protecting the confidentiality and integrity of protected health information (PHI).
However, its roots and evolution offer a broader picture of its importance in the healthcare industry.
The Act initially introduced a set of physical and privacy controls based on a ‘need-to-know’ principle. But the rise of digital technology in healthcare led to significant changes. In 2009, the American Recovery and Reinvestment Act (ARRA) passed the Health Information Technology for Economic and Clinical Health (HITECH) Act, giving birth to the Meaningful Use program, which promoted the adoption of electronic health record (EHR) systems.
This sparked a digital revolution in healthcare, with a surge in the use of EHRs. Consequently, HIPAA regulations had to evolve to cover electronic health information, incorporating additional provisions such as mandatory risk assessments and encryption.
Every practice and organization in the United States that handles protected health information is required to comply with HIPAA’s original regulations and those developed after the original announcement.
What Is the Purpose of HIPAA?
As the HIPAA acronym suggests, the Act focuses on two main areas: Accountability and Portability.
Accountability
The primary purpose of HIPAA’s Accountability side is to protect individuals’ medical information and ensure the privacy and security of their physical and electronic health records.
HIPAA establishes standards for how healthcare providers, insurance companies, and other entities handle protected health information (PHI) and electronic protected health information (ePHI).
It requires these entities to implement safeguards to protect PHI from unauthorized access or disclosure, and it gives patients the right to access and control their health information.
In addition to protecting patient privacy, HIPAA aims to improve the efficiency and effectiveness of the healthcare system by promoting electronic transactions and reducing administrative burdens.
By establishing consistent rules and requirements for handling PHI & ePHI, HIPAA helps ensure that healthcare providers and insurers can exchange information efficiently and accurately while protecting privacy rights.
Portability
The Portability portion of HIPAA mainly focuses on ensuring that individuals can maintain their health insurance coverage even when they change or lose their jobs. It achieves this through the following key provisions:
- Pre-existing conditions: HIPAA prohibits group health insurance plans from denying coverage or imposing waiting periods based on an individual’s pre-existing medical conditions. This means that individuals with existing health issues cannot be denied coverage, making it easier for them to move between jobs without the fear of losing insurance protection.
- Creditable coverage: The law also mandates that health insurance plans must recognize an individual’s previous coverage (known as creditable coverage) when assessing any pre-existing conditions exclusions. This provision ensures that people who have had continuous health insurance coverage are not penalized when switching jobs or insurance plans.
- Portability of coverage: HIPAA guarantees that employees and their dependents can maintain continuous coverage even when they change jobs, as long as they meet certain criteria, such as having had creditable coverage for a specific period. This portability ensures that people do not experience gaps in their health insurance, promoting more stable and consistent healthcare access.
- Limitation on exclusions: The act places limits on the duration of pre-existing condition exclusions in health insurance plans. This prevents insurance companies from imposing excessive waiting periods before covering certain medical conditions.
The Initial Purpose of HIPAA:
HIPAA is a law initially established to:
- Make healthcare delivery more efficient
- Enable portability in health insurance coverage
- Increase the number of Americans with health insurance coverage
- Combat fraud and abuse in health insurance
- Introduce tax breaks for medical savings accounts
- Incentivize and simplify the administration and management of health insurance
At its inception, HIPAA was divided into five main sections:
- Title I: HIPAA Health Insurance Reform – Title I seeks to protect health insurance coverage for those who lose or change jobs. It also disallows healthcare plans from withholding coverage to patients with preexisting conditions and setting lifetime coverage limits.
- Title II: HIPAA Administrative Simplification. Title II requires the HHS to establish national standards for processing electronic healthcare transactions. It also states that healthcare organizations must conduct transactions securely and comply with Privacy Rule regulations. Note: When most healthcare organizations talk about HIPAA compliance, they’re focused on adhering to Title II.
- Title III: HIPAA Tax-Related Health Provisions. Title III focuses on exemptions, deductions, and other tax-related areas.
- Title IV: Application and Enforcement of Group Health Plan Requirements. Title IV goes a step further in defining health insurance reform and specifies regulations for group health plans.
- Title V: Revenue Offsets. Title V touches on HIPAA regulations for company-owned life insurance and discusses the treatment of people who lose U.S. Citizenship for income tax purposes.
HIPAA has evolved and seen amendments and additions throughout the years, including the United States Department of Health and Human Services (HHS) Privacy Rule, which lays out standards for protecting sensitive physical and electronic patient health information.
In most cases, when someone refers to a HIPAA violation, they’re talking about the Privacy Rule.
When Was HIPAA Enacted?
Also known as the Kennedy-Kassebaum Act, HIPAA was first enacted by the United States Congress and officially signed into federal law by Bill Clinton on August 21, 1996.
Throughout its 25 years, HIPAA has been updated several times in both major and minor ways. The last major update was the addition of Health Information Technology for Economic and Clinical Health (HITECH) Act, which saw the introduction of the Breach Notification Rule in 2009 that requires HIPAA-covered entities to notify appropriate parties in the event of a data breach and the Omnibus Final Rule in 2013.
While there have been no major updates since 2013, as of 2023, there are proposed changes to the rule to decrease the administrative burden on HIPAA-covered entities, but those changes are still pending.
How Has HIPAA Evolved?
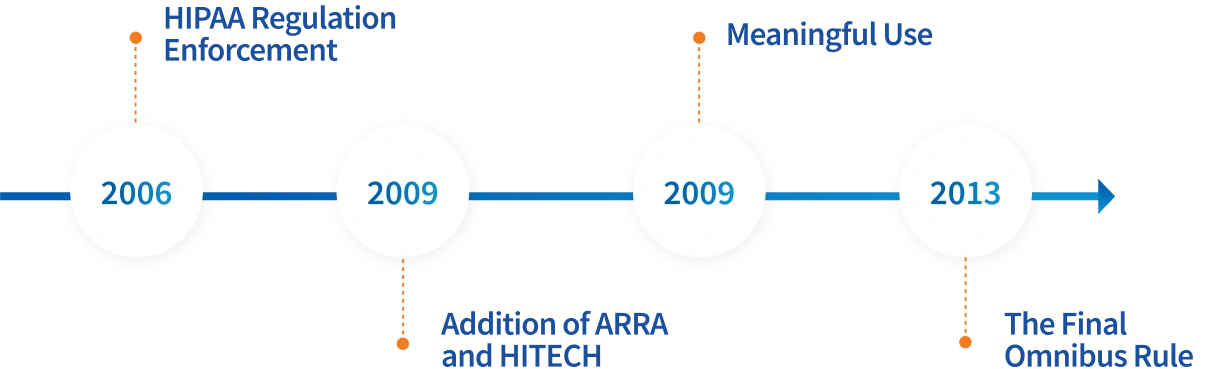
HIPAA has had major additions throughout the years:
- HIPAA Regulation Enforcement (March 2006): The Enforcement Rule allowed the Department of Health and Human Services (HHS) to investigate covered entities reported for failing to comply with HIPAA regulations. In addition to an investigation, the Enforcement Rule allows the Office for Civil Rights (OCR) to apply civil charges to entities that did not comply. This addition is what leads to major fines and alarming news headlines, like a $1.25 million penalty for a health system, a $75,000 fine for a Business Associate, and $4.8 million in hospital settlements, to name a few recent ones. In addition to OCR penalties, organizations often have to spend even more on recovering from a breach, so the costs add up. The best way to protect your business and meet regulations is by staying compliant.
- The Addition of ARRA and HITECH (2009): The American Recovery and Reinvestment Act (ARRA) was implemented in 2009 and included a vital addition to HIPAA enforcement, HITECH. HITECH introduced provisions for health information management, including the requirements for all breaches of ePHI affecting more than 500 individuals to be reported to the OCR within 60 days.
- Meaningful Use (2009): In addition to the Breach Notification Rule, HITECH introduced the Meaningful Use incentive program to encourage healthcare organizations to make their records electronic by implementing an Electronic Health Record (EHR). Today, that incentive program is called Promoting Interoperability.
- The Final Omnibus Rule (March 2013): The Final Omnibus Rule made clarifications to HIPAA and HITECH regarding the application of ePHI, as well as the wording within the acts themselves. The Privacy and Security Rules were also amended to modify the appropriate duration for obtaining a patient’s health information. Amendments included specifications for changing work practices in technological advances that were not applicable in 1996, such as mobile devices and telehealth.
Is HIPAA a Federal Law?
HIPAA is a federal law that applies nationally to all covered entities and business associates. Its regulations are enforced by the United States Department of Health and Human Services (HHS).
To learn more about who the federal law applies to, visit the Who Does It Apply To section below.
What Is PHI in HIPAA?
In the context of HIPAA, PHI stands for Protected Health Information. PHI refers to any individually identifiable health information created, received, or maintained by a covered entity or business associate while providing healthcare services.
What Is Considered PHI?
Under HIPAA, PHI includes various types of information, such as personal identifiers and health information. The Office of Civil Rights (OCR) has a list of 18 identifiers that, if present, qualify as PHI.
You can visit 18 HIPAA Identifiers: What They Are & Why Knowing Them Matters for an in-depth look at what constitutes PHI.
PHI also covers health information, which is anything related to an individual’s past, present, or future physical or mental health condition, the provision of healthcare services, or the payment for healthcare services.
This includes medical diagnoses, treatment records, prescriptions, laboratory results, and other information about an individual’s health status.
What Is Not Considered PHI?
The 18 identifiers are only considered PHI under HIPAA protection when used in the documentation associated with healthcare.
Health information without identifiers (such as a dataset of patient vital signs without any identifiers attached) is also not protected under HIPAA.
What Is ePHI and How Does It Relate to HIPAA?
Electronic Protected Health Information, or ePHI, is PHI transmitted, received, or stored electronically. This includes information in electronic medical records, emails, electronic claims, and other electronic formats and is protected under HIPAA the same way physical records are protected.
For the purpose of this resource, when you see “PHI” throughout the page, you can assume that it also refers to ePHI.
Who Does HIPAA Apply To?
Is HIPAA Important for Healthcare Entities of All Sizes?
Complying with HIPAA can feel burdensome, especially for smaller practices that often have all compliance processes fall on one person who likely has other things on their plate. HIPAA compliance requires immense know-how and bandwidth, and it can be difficult to figure out where to even start.
Because of that, some smaller entities might believe their size is too insignificant to be impacted by HIPAA or receive fines, and that going through the entire compliance process isn’t worth it.
But unfortunately, many small practices receive large fines, regardless of size. One New Jersey health center has to pay $30,000 to the OCR in 2023. Several small dental practices in Maryland paid a combined fine of over $140,000 in the last few years.
It’s critical for small practices to prioritize compliance as much as large entities. HIPAA’s requirements are there to help ensure that PHI is protected from unauthorized access or disclosure, and compliance processes are in place to help all entities avoid the costly penalties and legal liabilities associated with non-compliance.
What Are HIPAA-Covered Entities?
HIPAA applies to all covered entities, which can be healthcare providers, health plans, and healthcare clearinghouses that process and transmit health information electronically. Simply put, there is an immense range of different organizations impacted by HIPAA, from a single-office medical practice to a medium-sized healthcare software company, to a 100-hospital Integrated Delivery Network (IDN), and everything in between.
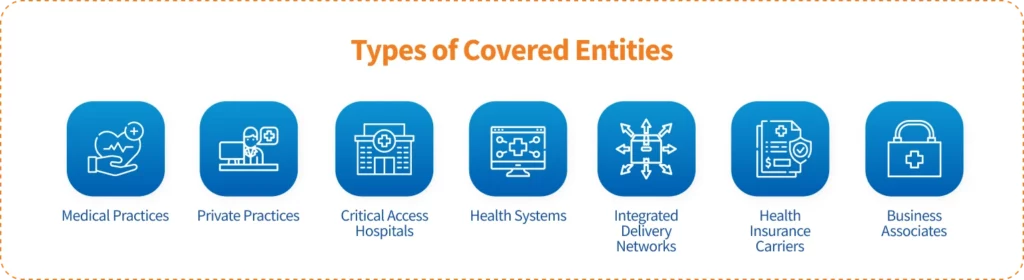
In other words, if an entity possesses personal patient health records or conducts certain financial transactions electronically, then it is considered a HIPAA-covered entity and must comply with HIPAA.
Even if these covered entities contract out to Business Associates (BAs), they are still obligated by Congress to abide by the Privacy Rule.
Are Business Associates Subject to HIPAA?
In short, yes. A Business Associate (BA) is an individual or entity that performs services or functions involving the use or disclosure of PHI on behalf of a covered entity under HIPAA. Examples include:
- Third-party service providers: Companies or individuals that provide services like billing, transcription, IT support, or cloud storage where they may have access to PHI.
- Consultants: External consultants who need access to PHI to perform their duties, such as legal, accounting, or compliance advisors.
- Health Information Exchanges (HIEs): Organizations that facilitate the exchange of PHI between different healthcare entities.
- Pharmacies: Pharmacies that process prescription orders and may have access to PHI.
- Medical equipment companies: Companies that provide medical devices and need access to PHI for maintenance or support.
- Healthcare software vendors: Companies that develop or offer healthcare software systems that store or process PHI.
Under HIPAA, Business Associates are considered separate entities from the covered entities, but they play an essential role in the healthcare ecosystem and may handle sensitive patient information. As such, they are required to comply with certain aspects of the HIPAA Privacy, Security, and Breach Notification Rules.
As with covered entities, failure to comply with HIPAA rules by a BA can result in significant penalties and legal consequences.
Does HIPAA Apply to Employers?
Because an employer often possesses private information of employees, such as social security numbers, addresses, and other sensitive data, many wonder if HIPAA also applies to non-health-related workplaces. Meaning, does your boss have to abide by HIPAA when handling your personal data?
It’s difficult to provide a blanket rule for when HIPAA applies to employers, but it generally does not. HIPAA only applies to employers in certain rare situations.
In other words, employers are not covered under HIPAA unless they provide healthcare services or operate a health plan that collects and maintains PHI. (For example, if an employer self-insures its employees’ health benefits, it may be considered a covered entity subject to HIPAA’s privacy and security regulations.)
However, employers are subject to other federal laws, such as the Americans with Disabilities Act (ADA), which restricts the collection and use of medical information in employment contexts.
Employers are generally prohibited from discriminating against employees based on their health status or medical history, and they must keep any medical information they receive confidential.
Does HIPAA Apply to Doctors’ Offices?
In short, yes.
HIPAA compliance is not determined by the size of your practice, but by the nature of the data you handle. This means that HIPAA applies to smaller practices and doctor’s offices.
All healthcare organizations that handle Protected Health Information (PHI), whether electronically or in paper format, are obligated to maintain compliance with HIPAA guidelines.
Does HIPAA Apply After Death?
HIPAA applies throughout a patient’s life AND for up to 50 years after an individual’s death. Any medical records containing the PHI and ePHI of individuals who have been deceased for over 50 years fall outside HIPAA’s protection.
Exceptions to this include disclosure of PHI required by law, for public health activities, or for research purposes, which can happen within the 50-year limitation.
Additionally, if a deceased patient’s family member requests access to patient records, PHI can be disclosed if the patient did not object while alive or if the disclosure is in the patient’s best interest.
When Does HIPAA Not Apply?
Most allowable HIPAA exceptions occur only in particular situations, and even the exceptions have their exceptions. Still, covered entities should be aware of exceptions to avoid withholding information in unique cases.
Some exceptions include:
- Personal Use
- Law Enforcement
- Research
- Colleges and Universities
- Emergency Situations
- State Law Contradictions
- Worker’s Compensation
For more information on these exceptions, visit HIPAA Exceptions: What You Need to Know.
Why Does HIPAA Matter?
HIPAA Enforcement
Who Enforces HIPAA?
HIPAA is enforced by the Office for Civil Rights (OCR), a division of the U.S. Department of Health and Human Services (HHS). The OCR ensures compliance with HIPAA’s privacy, security, and breach notification rules.
The OCR has the authority to investigate complaints and conduct compliance audits to assess whether covered entities and business associates adhere to HIPAA regulations. It can impose penalties, sanctions, and corrective actions on entities found to violate HIPAA requirements.
The OCR also provides guidance, education, and technical assistance to covered entities and business associates to help them understand and comply with HIPAA regulations. It aims to promote awareness of privacy and security practices, address individuals’ rights regarding their health information, and ensure the effective implementation of HIPAA safeguards.
Additionally, state attorneys generally have the authority to bring civil actions in federal court to enforce HIPAA or obtain damages on behalf of residents of their respective states. However, the primary enforcement responsibility lies with the OCR at the federal level.
Who Handles the Prosecution of HIPAA Violators?
While the OCR handles civil violations of HIPAA and can levy fines and other corrective actions, criminal violations of HIPAA are regulated by the United States Department of Justice (DOJ). If an entity “knowingly” violates HIPAA, meaning they sell, transfer, or use identifiable health information for their own commercial advantage or to purposefully cause harm, it’s considered criminally liable and thus falls under the DOJ’s jurisdiction.
What Happens If I Do Nothing?
While it may be tempting to completely avoid implementing HIPAA procedures or conducting risk assessments, covered entities who ignore HIPAA compliance entirely can face severe consequences.
These consequences can affect organizations of ALL sizes, and may include:
- Financial penalties: Non-compliance risks significant fines from the OCR, which can reach up to $1.9 million per calendar year. This can be exacerbated by costly incident management expenses.
- Increased Vulnerability: Neglecting HIPAA compliance makes healthcare organizations more vulnerable to data breaches, cyberattacks, ransomware, and other damaging security incidents that harm both patients and the organization.
- Legal consequences: HIPAA does not provide a private right of action, meaning that individual patients cannot directly sue for violations of HIPAA. However, ignoring HIPAA can leave organizations vulnerable to legal action from patients suing for damages based on state law surrounding privacy or medical malpractice.
- Loss of trust and reputation: Data breaches erode public trust, leading to a loss of clients and long-term damage to an organization’s reputation. Public HIPAA violations can also affect your organization’s Net Promoter Score (NPS), which measures overall patient satisfaction.
Violating HIPAA
What Is a HIPAA Violation?
A HIPAA violation refers to any action or failure to act that violates the rules and regulations outlined in HIPAA. There are several types of HIPAA violations, including:
- Unauthorized Disclosure: Sharing or disclosing PHI without the individual’s consent or a valid reason for disclosure. This can occur through oral, written, or electronic means.
- Lack of Safeguards: Failing to implement appropriate administrative, physical, and technical safeguards to protect PHI from unauthorized access, theft, or loss. Examples include inadequate security measures, lack of encryption, or weak passwords.
- Improper Access: Gaining access to PHI without proper authorization or for reasons unrelated to the individual’s role in providing healthcare. This includes “snooping” into a patient’s medical records out of curiosity or personal interest.
- Breach Notification Failure: Failing to provide timely notification to affected individuals, the HHS, and, in some instances, the media following a breach of unsecured PHI.
- Insufficient Training and Compliance: Neglecting to provide adequate HIPAA compliance training to employees, resulting in ignorance of privacy and security requirements or improper handling of PHI.
Some HIPAA violations are easier to prevent than others.
Regardless, the first steps you should take are to:
- Be aware of the most common HIPAA violations and solutions to avoid them.
- Assess your own practices through a Security Risk Assessment (SRA). If it is your first time conducting an SRA, consider a hiring a consultant to guide you or your HIPAA compliance officer through the requirements.
What Is a Breach of HIPAA?
Violating HIPAA can often lead to a breach, which refers to the unauthorized acquisition, access, use, or disclosure of PHI that compromises the security or privacy of the information. A breach can occur in various ways, such as:
- Unauthorized Access: When an individual gains access to PHI without proper authorization or a legitimate need to know. This can include accessing patients’ medical records without permission or for personal reasons.
- Theft or Loss: When physical devices or records containing PHI, such as laptops, smartphones, paper files, or storage media, are stolen, misplaced, or lost. If the PHI is not adequately encrypted or protected, it can result in a breach.
- Hacking or IT Security Incidents: When cyberattacks or security incidents occur that lead to the unauthorized access, acquisition, or disclosure of ePHI. This can include ransomware attacks, phishing, and other similar incidents.
- Improper Disposal: When PHI is not disposed of securely, such as failing to shred or destroy paper records properly or not wiping electronic devices containing PHI before disposal.
For more information on what to do if your organization experiences a breach, refer to our section below, “What should you do if you have a security breach?”.
What’s the Difference Between a Data Breach and a HIPAA Violation?
While both data breaches and HIPAA violations can involve unauthorized access or disclosure of protected health information (PHI), they are distinct from one another in terms of their causes, consequences, and regulatory implications.
Data breaches are security incidents through which unauthorized individuals gain access to sensitive information, such as PHI. These breaches can occur due to various reasons, such as hacking, theft, loss of devices, malicious intent, or human error.
The consequences of data breaches include reputational damage, legal liability, financial loss, and data.
In contrast, HIPAA violations constitute any action or inaction that directly violates HIPAA regulations. These violations may or may not involve a data breach. The consequences of a HIPAA violation can include civil penalties, criminal penalties, corrective action plans, and reputational damage.
What Happens if an Entity Is Not HIPAA Compliant?
HIPAA non-compliance can result in serious and lasting consequences for organizations of all sizes, no matter how small.
Civil Penalties
The Office for Civil Rights (OCR) can fine covered entities for HIPAA non-compliance. HIPAA violations are classified into four distinct tiers based on the level of culpability involved, with each tier subject to different fines.

Tier 1: Lack of knowledge Minimum fine of $127 per violation up to $63,973
Tier 2: Reasonable cause and not willful neglect Minimum fine of $1,280 per violation up to $63,973
Tier 3: Willful neglect, if violation is corrected within 30 days Minimum fine of $12,794 per violation up to $63,973
Tier 4: Minimum fine of $63,973 per violation, up to $1,919,173
The calendar year cap for violations related to a specific HIPAA provision is $1,919,173.
If a covered entity violates multiple, separate provisions of HIPAA, each violation is considered separately and could be subject to its own maximum cap of $1,919,173.
Criminal Penalties
Criminal penalties are administered in the case of knowing and willful violations of HIPAA. These penalties are pursued by the Department of Justice and can lead to fines and imprisonment.
Individuals who risk facing criminal penalties for HIPAA violations include healthcare providers, healthcare staff, health plan administrators, executives, and employees of business associates who knowingly and willfully obtain or disclose protected health information (PHI) without authorization.
Even in the case of small doctor’s offices, physicians, nurses, administrative staff, or other employees may face criminal charges for willful HIPAA violations.
Penalties range from $50,000 and one year in prison for knowingly obtaining or disclosing PHI, to up to $250,000 and 10 years in prison for violations committed with the intent to sell, transfer, or use PHI for commercial advantage, personal gain, or malicious harm.
Corrective Action Plans
The Office for Civil Rights (OCR) may require HIPAA violators to implement a Corrective Action Plan (CAP). A Corrective Action Plan is a set of steps a healthcare entity must follow to remedy a HIPAA violation and prevent future violations. This typically involves policy updates, staff training, and regular reporting to OCR.
Non-compliance with the terms of a CAP can further escalate penalties.
Legal Vulnerability
Patients whose privacy has been breached may have the right to sue the offending organization for damages resulting from the violation, leading to substantial settlements.
Attorney and litigation fees can compound the overall cost of HIPAA non-compliance, while also draining valuable time and resources.
Patient Mistrust
Breaches can give rise to significant loss of patients and tarnish an organization’s reputation. Regaining public confidence after a breach can be a long, challenging process. While there are no specific financial penalties attached, erosion of patient trust alone can cause small practices to fail.
Other penalties and consequences from failure to maintain HIPAA compliance may include a raised cybersecurity insurance fee and more intensive OCR monitoring into the future.
How Can HIPAA Violation be Reported?
According to the HHS website, anyone can file a HIPAA complaint if they believe a covered entity or business associate violated HIPAA. The OCR can then investigate complaints.
Complaints can be filed in writing (through the mail, e-mail, or fax), but the HHS recommends doing so online through the OCR’s complaint portal. The complainant must file their complaint within 180 days of witnessing the HIPAA violation unless they can prove, with good cause, that they needed to file after 180 days.
Complaints must include:
- Information about the complainant
- Details of the complaint
- Any additional information that might help OCR when reviewing the complaint
Reporting a HIPAA violation is a protected action under HIPAA. This means that covered entities (such as medical practices, hospitals, business associates, and more) are legally prevented from retaliating against a complainant and could face additional consequences if they retaliate or threaten the complainant in some way.
Can You Get Fired for Violating HIPAA?
Termination due to a HIPAA violation is a potential outcome based on the severity of the violation, organizational procedures, and managerial discretion.
How Many Instances of Non-Compliance Does It Take to Get a Fine?
Under HIPAA regulations, a single instance of non-compliance may result in financial penalty. The OCR issues fines on a case-by-case basis, considering the perceived level of negligence and the severity of the violation.
Repeated or unaddressed non-compliance can lead to escalating fines, with a maximum penalty of $1.9 million per year for violations of an identical provision.
HIPAA Compliance
What Is HIPAA Compliance?
HIPAA compliance refers to adherence to the regulations and requirements outlined in the Act.
Compliance entails following the guidelines and safeguards established by HIPAA to protect the privacy, security, and integrity of individuals’ protected health information (PHI).
To achieve HIPAA compliance, covered entities and their business associates must implement policies, procedures, and technical measures that ensure the confidentiality and security of PHI.
How Can a Covered Entity Be HIPAA-Compliant?
Becoming HIPAA-compliant might seem like a Herculean task, but by taking it step-by-step, every covered entity or Business Associate can achieve full HIPAA compliance. For medical practices, we would recommend following these steps to get started:
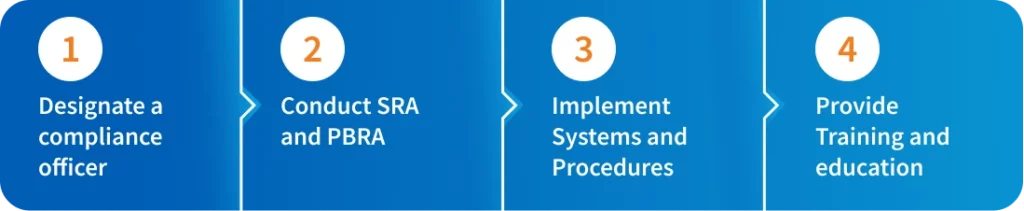
- Designate a HIPAA Compliance Officer: Assign someone in your office or an outsourced expert to be responsible for overseeing and executing HIPAA compliance.
- Conduct a Security Risk Assessment (SRA) and Privacy & Breach Risk Assessment (PBRA): To gain visibility into what you’re currently doing to stay compliant and where there might be some gaps, conduct annual risk assessments to understand areas of need.
The SRA will allow you to comply with the Security Rule, while the PBRA helps ensure compliance with the Privacy and Breach Notifications Rules.
With the help of a tool like HIPAA One ®, you can complete your assessments in a guided manner, so if it’s your first time, you don’t have to figure everything out alone.
Then, subsequent assessments can be heavily automated based on stored data from previous years, so you can automate the drudgery and get reusable, trackable results. - Implement Systems and Procedures: Based on the results of your assessment, it’s time to make sure you have the processes in place to remain compliant.
How do you ensure that PHI isn’t inappropriately shared, or devices don’t get lost? Included in your processes should be Business Associate Agreements (BAAs), which guarantee that the BAs you work with remain compliant.
With HIPAA One ®, you’ll receive recommendations on what to improve and how to do so based on your assessment results so that you’re not just checking a box but rather becoming actively compliant through expert help. - Provide Training and Education: Lastly, based on your systems and processes, provide training to workforce members on HIPAA regulations, privacy practices, security protocols, and the handling of PHI.
This helps ensure that employees know their responsibilities and understand how to protect PHI appropriately.
For larger organizations seeking to institute a culture of compliance, complete the same steps as medical practices, with a few key editions:
- Conduct your SRA and PBRA with the help of an expert consultant who can dig into your technical, administrative, and physical risks. Medical practices might also benefit from the help of a consultant, but for large organizations, it’s a necessity.
- Your SRA should apply to every location in your organization that legally needs it. In other words, only conducting an assessment on a few entities and extrapolating those results on to the rest (also known as sampling) is an unnecessary risk, especially given the availability of automation platforms that can streamline assessments.
- Because PHI might spread far, maintain an inventory of all systems that contain PHI and monitor closely and frequently.
- Stay mindful of third-party risks by covering all of your major systems that use PHI.
- Show meaningful remediation progress year-over-year and demonstrate that all critical gaps were fixed within 90 days, if possible.
How to Assign a Compliance Officer
What is a HIPAA Compliance Officer?
In the past, many organizations had their IT team handle minimal compliance measures. But as cybersecurity breaches steadily increase, more and more entities hire an in-house or outsourced Compliance Officer.
A HIPAA Compliance Officer (CO), also known as a Privacy Officer or Security Officer, is an individual designated by a covered entity or business associate to oversee and ensure compliance with the regulations outlined in HIPAA.
Their primary responsibility is to manage and implement HIPAA compliance measures within the organization.
Compliance Officers handle:
- HIPAA policy development: Start with conducting a comprehensive assessment of your organization’s current data practices and potential risks to identify areas that need to be addressed in your HIPAA policy development.
- Training and education: Begin by developing a clear and engaging HIPAA training program tailored to different roles within the organization to ensure all employees understand their responsibilities and the importance of safeguarding protected health information.
- Privacy and security audits: Start by reviewing and familiarizing yourself with the HIPAA Privacy and Security Rule requirements, and then conduct a thorough internal audit of your organization’s policies, procedures, and technical safeguards to identify any potential compliance gaps.
- Incident management and response: Begin by establishing a detailed incident response plan that outlines clear procedures for identifying, reporting, and responding to potential HIPAA breaches, ensuring all staff members are well-trained on its implementation.
- HIPAA compliance monitoring and enforcement: Start by implementing regular monitoring and auditing processes to assess your organization’s compliance with HIPAA regulations, and establish a clear enforcement policy outlining consequences for non-compliance to promote a culture of adherence to privacy and security standards.
- Business Associate management: Begin by conducting a comprehensive risk assessment of your business associates, ensuring they have appropriate safeguards in place to protect protected health information and have signed HIPAA-compliant business associate agreements.
Having a designated HIPAA Compliance Officer demonstrates an organization’s commitment to protecting patient privacy and security, which is an important part of compliance.
This role helps ensure that the organization is aware of and adheres to HIPAA regulations, mitigating the risk of data breaches, penalties, and reputational damage.
How to Choose a Compliance Officer
When choosing a HIPAA compliance officer, it is crucial to identify an individual with a strong understanding of healthcare regulations and privacy laws.
Look for candidates with prior experience in healthcare compliance or a related field, as well as a demonstrated ability to interpret and implement HIPAA requirements effectively.
The ideal candidate should possess excellent communication skills to educate and train staff members on HIPAA policies and procedures, along with the capacity to lead and coordinate compliance efforts across the organization.
Additionally, the chosen HIPAA compliance officer should have a keen eye for detail and a proactive approach to identify potential compliance gaps and risks.
Their role will involve regularly assessing the organization’s compliance status, conducting audits, and implementing corrective actions when necessary.
A commitment to staying updated with evolving HIPAA regulations and industry best practices is essential, ensuring the organization remains continuously compliant and upholds the highest standards of patient data protection.
As technology continues to evolve and the landscape of HIPAA compliance grows increasingly complex year by year, organizations should consider dedicated HIPAA compliance software to support the Compliance Officer role.
Such software can not only streamline and automate the maintenance of required documentation and records, but can also organize key elements such as policies, procedures, risk assessments, training records, and incident reports in a centralized location.
Task a Compliance Officer to service as a central point of contact to oversee HIPAA compliance within an organization. This role is key to maintaining a culture of compliance even within small practices.
While a demanding role, compliance officers can utilize software solutions to track access to PHI, detect suspicious activities, and ensure compliance with privacy and security policies. The software can help identify and address potential breaches or unauthorized access, as well as establish clear steps for remediation.
Organizations can also choose to outsource the Compliance Officer role, working with a trusted HIPAA partner. This outsourced partner can work in tandem with your organization and software tools to ensure full compliance.
HIPAA Compliance Training
What Is HIPAA Compliance Training?
HIPAA training aims to educate healthcare professionals, employees, and other relevant people about the requirements and best practices for safeguarding PHI.
The training covers various aspects of HIPAA regulations, including the Privacy Rule, Security Rule, and Breach Notification Rule.
Receiving the proper HIPAA compliance certification and training is not only critical for helping individuals understand and follow HIPAA compliance protocols but is also a proof point for organizations that experience a breach and need to show the OCR that they have adopted measures to prevent a cybersecurity attack.
It is important to note that HIPAA compliance training may vary depending on individuals’ specific roles and responsibilities within an organization. Healthcare providers, business associates, and their employees may receive different levels of training tailored to their respective functions.
Advanced HIPAA compliance software solutions will oftentimes offer customizable training as part of the packaged features.
Compliance Officers should seek out a solution with built-in training tools that ensure your team’s training stays up to date through automated reminders, real-time training reports, and regular quizzes and assessments.
How to Conduct Risk Assessments
Understand the Difference: What Is a HIPAA SRA vs. PBRA?
One of the most important parts of modern-day HIPAA is its risk assessments.
The security risk assessment (SRA) enables you to assess, identify, and take steps toward mitigating risk and filling potential gaps and threats in your security infrastructure.
Entities are required to conduct an SRA at least annually, though if there are major organizational changes (such as the introduction of a new software to hold data, for example), then both assessments should be conducted again as needed.
A privacy and breach risk assessment (PBRA) helps you determine if data from your organization has been breached, the severity of the potential breach, and what actions you can take to start remediating the breach and protecting patient privacy.
Entities are strongly encouraged to conduct a PBRA at least annually. However, if they choose to skip conducting a PBRA, they must disclose every breach or prohibited access to PHI to the OCR. Due to the potential consequences, it is not recommended to neglect conducting an annual PBRA.
Choose the Right Software
When conducting self-guided HIPAA risk assessments, it’s easy to be overwhelmed by the intricacies of HIPAA compliance and ever-evolving compliance regulations.
Look for software that makes conducting assessments an easy, step-by-step process. The solution should have built-in automation, remediation steps and recommendations, and let you import and access previous results to save time.
Choose the Right Certified Assessor
Should I do my SRA and my PBRA by myself?
For small practices especially, the prospect of conducting a Security Risk Assessment (SRA) and Privacy Breach Risk Assessment (PBRA) completely in-house may seem appealing, offering potential cost savings and a sense of direct control.
However, conducting these assessments in-house may actually be less effective than outsourcing the process or incorporating an automated compliance solution.
For smaller practices especially, the first assessment can be overwhelming, and having an expert guide you through the steps is critical in delivering a complete, accurate assessment. For larger organizations, having the help of a certified assessor or consultant is the best way to dig deep into all data and conduct a proper assessment.
In other words, conducting a successful assessment starts with choosing the right partner. Partnering with a trusted HIPAA compliance expert can save you time, reduce non-compliance risk, and help you avoid hefty penalties and legal nightmares. As a result, choosing a compliance consultant to help you start your journey on the right foot will be cheaper in the long run.
Then, as your knowledge base and tool stack expand, organizations can transition to a self-guided, software-driven assessment process occasionally supported by a consultant.
What Should You Do if You Have a Security Breach?
In case of a security breach which involves unauthorized disclosure of PHI, organizations must adhere to specific remediation and incident management procedures.
Security Rule Breach: What Should I Do?
The Security Rule outlines specific safeguards for electronic PHI (e-PHI), addressing technical, physical, and administrative vulnerabilities.
In the event of a HIPAA security breach, organizations must promptly identify and rectify the vulnerabilities that led to the breach to maintain Security Rule compliance. This may include conducting a thorough risk analysis to identify how the breach occurred, implementing stronger technical, physical, and administrative safeguards as necessary, and documenting all actions taken to remediate the breach and improve security measures.
Privacy Rule Breach: What Should I Do?
The Privacy Rule focuses on regulating the use and disclosure of protected health information (PHI)
Following a breach, organizations must promptly follow Breach Notification rule procedures and notify affected individuals.
Organizations should also assess the nature and extent of the PHI involved, identify the parties involved in the breach, and determine whether the PHI was actually acquired or viewed.
Many HIPAA software solutions help organizations to track and document these security incidents, breaches, and unauthorized disclosures of PHI. They assist in generating incident reports and provide a framework for timely notification and response.
Creating a Culture of Compliance
Systems and Procedures
One of the most important elements of a strong compliance culture is clearly implemented and documented rules, systems, and procedures in place. These procedures should be part of training and enforceable, and might include:
- Implementing role-based access controls to limit access to PHI, ensuring that employees can only access information necessary for their specific job functions.
- Utilizing encryption and other security measures to protect electronic PHI and ensure that physical PHI is securely stored and accessed.
- Creating an incident response plan that outlines the steps to be taken in the event of a data breach or potential security incident, including reporting procedures and corrective actions.
- Developing and maintaining detailed policies and procedures that cover various aspects of HIPAA compliance, such as data security, breach notification, and employee roles and responsibilities.
- Establishing a confidential reporting mechanism for employees to raise concerns or report potential violations without fear of retaliation.
- Clearly communicating the consequences of HIPAA non-compliance, which may include disciplinary actions, up to and including termination, for serious violations.
Training and Awareness
Every team member, regardless of their role, should be thoroughly educated about HIPAA regulations and their personal responsibilities in protecting patient data. Make certain that all staff understand the repercussions of non-compliance: both for the practice and for them personally.
This may involve regular training sessions, updates about changes in regulations, and discussions about real-world scenarios that your practice might encounter.
This software may provide training modules or tools to educate the workforce on HIPAA regulations, best practices, and their responsibilities in protecting PHI. This helps track and document employee training, ensuring ongoing compliance education.
Business Associate Agreements
A Business Associate Agreement (BAA) under HIPAA is a key safeguard for your company. This legal document establishes explicit parameters for the use and protection of Protected Health Information (PHI), ensuring that your business associates adhere to specified privacy and security standards.
These BAA agreements can be managed manually, or through a dedicated HIPAA compliance software focused on managing safeguards between vendor and partner compliance.
BAAs are not merely regulatory requirements— in the case of a PHI breach triggered by a Business Associate (BA), your company may be protected from reputational and legal liability. However, BAAs are sometimes not enough to guarantee an organization’s protection if their BA violates HIPAA.
For that reason, it’s important for organizations to conduct due diligence and understand the reputation of the BAs they might work with. Large organizations might consider using third-party risk management (TPRM) to monitor, audit, and remediate the risks associated with all external interactions. Entities of all sizes should require guarantees that their BA is serious about HIPAA compliance.
HIPAA Compliance Software
How Can You Find HIPAA Compliance Software?
Before investing time and money in HIPAA compliance software, you’ll want to conduct extensive research to make sure you’re picking a solution that will meet your needs. Conduct preliminary research, get referrals and recommendations from other entities, and consult compliance experts and vendor directories.
It’s also essential to consider factors such as ease of use, scalability, integration capabilities, data security measures, customer support, and cost-effectiveness. Additionally, ensure that the software vendor provides regular updates and stays updated with evolving HIPAA regulations.
When looking for your solution, make sure to pick software the has the following features and capabilities:
- Self-Service & Guided Execution: Software should be flexible and offer an easy, hybrid approach to compliance, allowing you to complete assessments and other compliance processes on your own or get the support of a Certified Assessor as needed. This helps manage the cost of overall ownership and makes managing risk year-round much simpler.
- Reference Policies & Procedures: Using pre-written HIPAA policy documents saves more than 80% of the effort required to complete the SRA. Your software should have a policy library with documents that align with relevant regulations and can be customized. Documents might include employee onboarding and offboarding procedures, the frequency of safeguard reviews, and more.
- Built-In Automation: An effective compliance solution should include built-in automation for task delegation, task status, reminder alerts, follow-up notifications, and more to keep your team on track and ensure that no compliance tasks fall through the cracks.
- Remediation Status & Tracking: A large component of HIPAA compliance is proving that you’ve taken the proper actions to maintain a strong security risk posture. Your software should show and track your remediation progress so that you can easily demonstrate a culture of compliance, if necessary, even if you’re unable to immediately remediate all risks.
- Historical Data Importing: Software should allow you to import previous assessment results for a fleshed-out picture of your historical data, and automation can help make sure you don’t have to input the same information into your assessments year after year.
- Multi-Location Support & Parent-Child Dynamic Synchronization: Larger organizations usually deal with numerous entities with different tax ID numbers. The government requires a separate risk assessment for each entity, and parent/child sharing functionalities enable you to produce an SRA for every sub-entity without needing to copy and paste redundant policies, gaps, remediation statuses, and other data. Plus, a change to one SRA will automatically apply to the rest, so you’ll never have to manually edit hundreds of documents.
- Practical Recommendations: Assessments alone are not enough. Remediation is where true compliance happens, so your compliance solution should give practical recommendations to actively help you with remediation and prevent breaches or other incidents.
- Lower Cost of Ownership: The right platform should be user-friendly and make third-party collaboration simple, giving you the flexibility to choose a hybrid approach to compliance. This can lower the cost of ownership over time by allowing you to forgo the expense of third-party collaboration whenever you choose while still giving you a comprehensive suite of tools to remain compliant.
- Privacy & Security Risk Assessment in One Product Family: Look for a solution that supports both your security risk assessment and your privacy and breach risk assessment. Having separate platforms for the assessments wastes time and causes friction, so keeping them together creates better and more streamlined compliance processes.
- Proven Security and Compliance Track Record: Your software should have a long-standing reputation in the industry. Find out how long the company has been in business, if they have a successful track record in security and compliance performance, how many clients they serve, their audit success rate, and other indicators that will help prove their effectiveness.
- Continuous Federal & State Regulation Updates: Your product has little value if it doesn’t help you comply with current regulations. Because state and federal regulations change constantly, look for a product that updates regularly so you never fail to comply with a critical regulation.
- Meets OCR Guidelines for HIPAA Compliance: Software should support specific HHS regulations, including:
- Security Risk Assessment regulations per CFR 164.308(a) (1)
- Privacy Breach Risk Assessment regulations per CFR 164.524
- Scalable for Enterprises: For larger organizations, your solution should be scalable and give you the opportunity to go beyond HIPAA and move toward HISTRUST, TPRM, NIST, and other regulations. It should also let you see all of your compliance and risk assessments through a single pane of glass so that you can understand and prioritize remediation actions.
Should You Rely Solely on HIPAA Compliance Software?
It’s important to note that while HIPAA compliance software can support your organization’s compliance efforts, it does not guarantee full compliance on its own.
The best way to achieve full compliance is to take a blended approach by using software and expert guidance to set you up.
Many organizations that use software to complete their security risk assessment don’t fully understand the assessment questions. Without an expert looking over their documents, they might not be fully compliant, even if a tool tells them they are.
Having an expert look over your compliance systems the first time you use them is valuable. After that, you can use a “TurboTax” approach and only have an expert revisit your validated assessment when changes arise in your system (which might be more than once a year).
By doing this, you can ensure that you’re not just checking off compliance boxes but instead building a true culture of compliance.
HIPAA Compliance: Conclusion
Understanding and maintaining HIPAA compliance is crucial for safeguarding sensitive patient information and ensuring the security and integrity of healthcare organizations. Throughout this page, we’ve covered various aspects of HIPAA compliance, providing you with valuable insights and actionable tips to help you navigate the complex regulatory landscape effectively.
As you strive to achieve and sustain HIPAA compliance, keep the following tips in mind:
- Stay Updated: Continuously monitor updates to HIPAA regulations and guidelines to ensure your organization stays current with the latest requirements and best practices (or better, use a software that will alert you when relevant updates happen)
- Conduct Regular Training: Train all employees on HIPAA rules, data security protocols, and the importance of safeguarding PHI. Regular training sessions can reinforce compliance awareness and reduce the risk of accidental breaches.
- Perform Risk Assessments: Regularly assess your organization’s security measures, vulnerabilities, and potential risks. Identify weak points and address them promptly to fortify your defenses against data breaches.
- Develop Comprehensive Policies: Create robust policies and procedures that align with HIPAA requirements. Tailor these policies to fit your organization’s unique needs and make sure all staff members understand and adhere to them.
- Use Technology Wisely: Leverage HIPAA-compliant software and tools to manage patient information securely. Ensure your IT infrastructure meets the necessary security standards.
- Implement Data Encryption: Encrypt all sensitive data, both in transit and at rest, to protect it from unauthorized access and ensure its confidentiality.
- Establish an Incident Response Plan: Develop a well-defined incident response plan that outlines steps to be taken in case of a security breach. This will help minimize the impact and facilitate a swift and efficient response.
Compliance is an ongoing commitment that requires continuous effort to adapt to evolving regulations and industry best practices. With the right solution and trusted partner, you can strengthen your security, safeguard patient data, and protect your organization from the damaging consequences of both non-compliance and data-breaches.
To streamline your HIPAA compliance journey and ensure comprehensive adherence, try Intraprise Health’s HIPAA One compliance solution. HIPAA One offers a robust and user-friendly platform that simplifies compliance management, provides expert help as needed, automates risk assessments, and includes tailored policies and procedures aligned with HIPAA regulations. Take the first step towards enhanced cybersecurity and regulatory compliance by booking a free guided demo of HIPAA One today.








