
HIPAA One® Security Risk Assessment Tool
- 10,000+ Assessments Performed
- 100% OCR Acceptance
- 3x YoY Efficiency Gains
Get a HIPAA One Demo
Trusted by 64,000+ Providers




















Simplify your HIPAA Security Risk Assessment
Our HIPAA risk assessment offering combines Intraprise Health’s highly rated security services with our industry leading HIPAA Security Risk Assessment software. Automate and simplify your compliance with the help of our HIPAA One® software.
Increase capabilities and save time while lowering costs
Many healthcare organizations use time-consuming and inaccurate manual processes for compliance, such as complicated spreadsheets and uninspired templates.
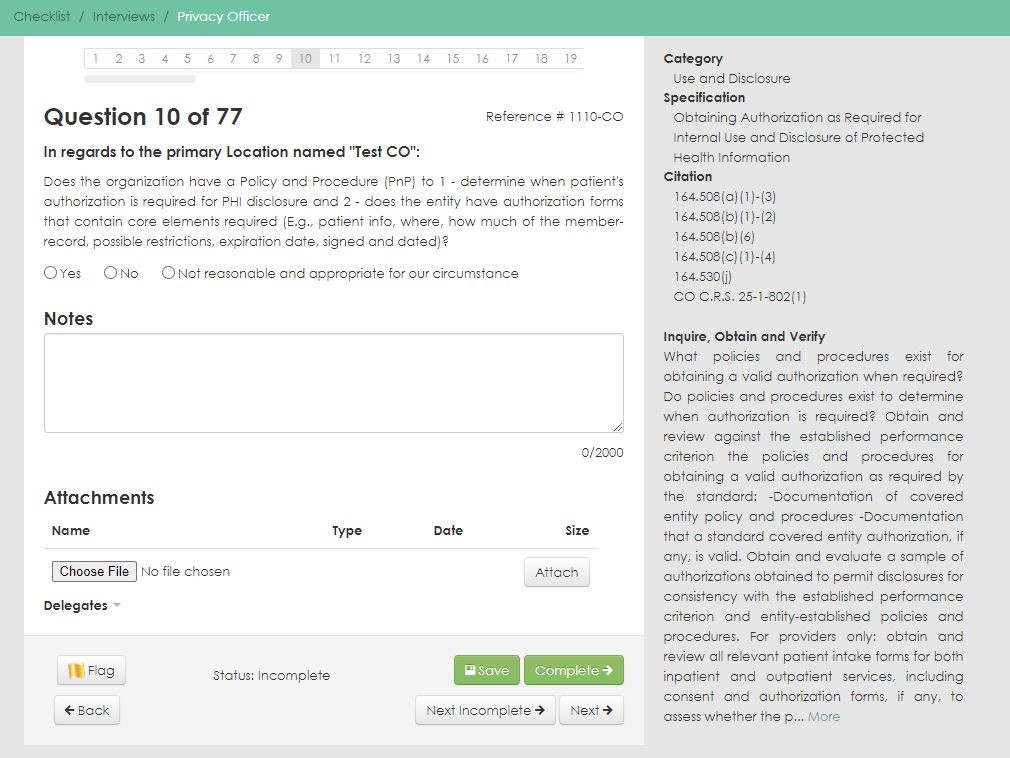
Simple, automated, and affordable, our HIPAA Security Risk Assessment focuses on efficiency as well as accuracy, helping remove the administrative burden of compliance with:
- Pre-configured healthcare assessments
- Automated task reminders
- Real-time reporting & final reporting
- Comprehensive vendor management
- Customizable templates, policies, and procedures
- Centralized documentation for covered entities, BAs, contractors, and more
Mitigate Risks Independently or With the Help of Assessors
Our cloud-based software follows OCR Audit Protocol and is based on NIST-methodologies to help organizations appropriately respond to and mitigate risks.
You can independently complete your HIPAA assessment using the HIPAA compliance tool’s templates and audit-proof automation.
If you would like assistance, our Assessors will work with you in a collaborative, standards-based, and compliance-aware approach to assess your information security and risk management program to help you lower your risk.
Your guided assessment will kick off with a call between our experts and your support team to walk through the HIPAA compliance solution and assist with documentation uploading. Then, after you fill out the assessment, we’ll review, verify, and validate the information in the assessment to ensure that it’s ready.
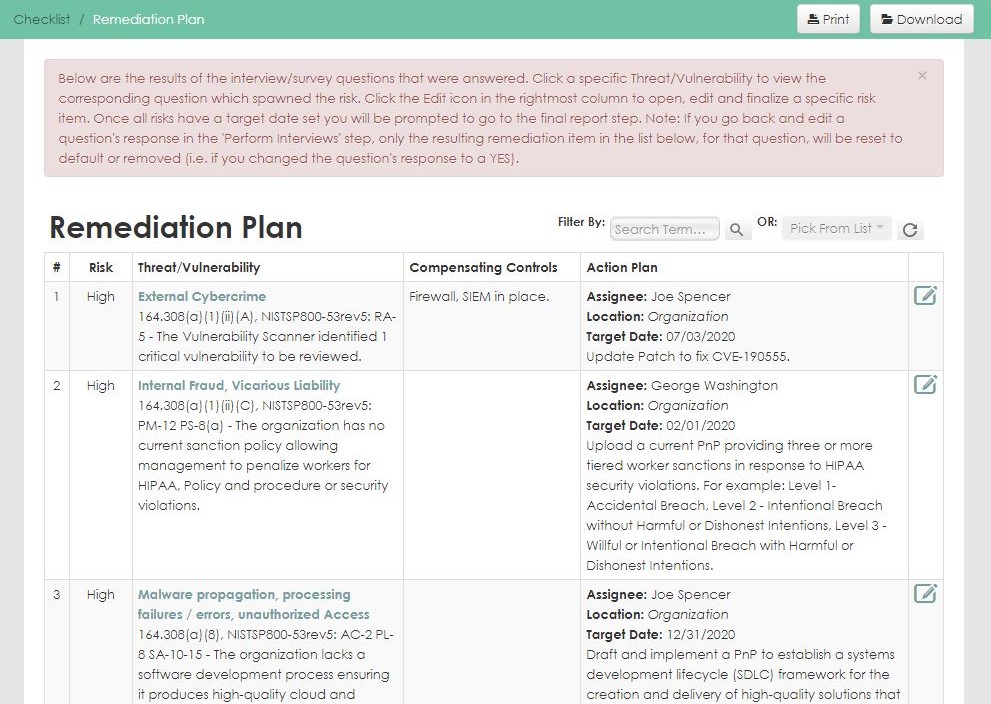
Our HIPAA Security Risk Assessment Tool Will Help You:
- Identify threat sources and events
- Identify vulnerabilities
- Determine likelihood of breach occurrence
- Determine magnitude of impact
- Understand your risk
Backed by our team of certified professionals, we provide the structure, detail, and clarity you need to:
- Make an evaluation of your HIPAA/HITECH compliance
- Create the full documentation of the state of security controls
- Meet the legal requirements for Meaningful Use
- Find gaps that are a true risk for the business
- Come up with a remediation roadmap which is practical
- Establish a working and sustainable model for information security and privacy
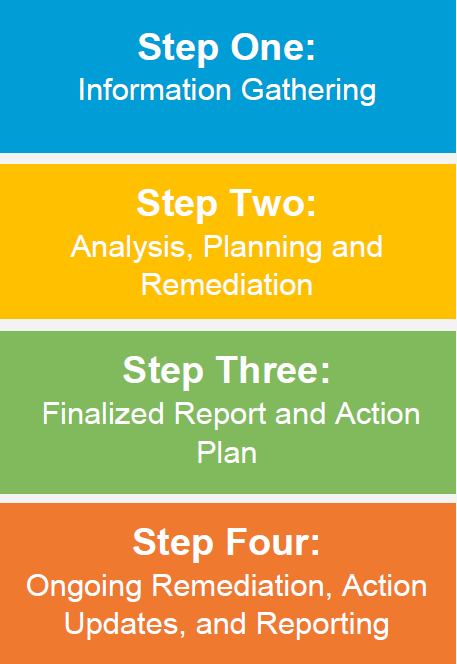
HIPAA Risk Assessment Process

HIPAA Security Risk Assessment Engagement Types
Guided Assessment
Independently Conduct your Risk Assessment Utilizing HIPAA One
Our Guided SRA Includes:
- System workflow guides you through the assessment
- Access to policy and procedure template library
- System-generated risk ratings and remediation recommendations
- Customizable report of findings
- Product usability support provided by your guide
Validated Assessment
Remote and/or On-Site Assessor-Managed Risk Assessment Utilizing HIPAA One
Our Validated SRA Includes:
- Assessment readiness support provided by your assigned Assessor
- System workflow guides you through the assessment
- Access to policy and procedure template library
- Risk assessment validated by your Assessor(s)
- Remediation recommendations reviewed and approved by your Assessor(s)
- Assessor signs off on report of findings
- Technical and executive level ROF presentations
- Physical walk-through guidance (if on-site)
Every HIPAA Security Risk Assessment follows OCR Audit Protocol and maps findings to NIST SP 800-53
Advantages of the HIPAA One® Cloud Software:
- Step-by-step guided approach to HIPAA compliance
- Up-to-date compliance software including citations for HIPAA, NIST, and 42 CFR Part 2
- Access to our team of certified Assessors
- Widely used among healthcare organizations of all sizes
Enhanced HIPAA SRA Tool Capabilities Include:
- Automated task reminders
- HIPAA assessment question assignment and prioritization and risk calculations
- Remediation tracking and action history
- Real-time, custom reporting
- Year over year import of assessments
Why Healthcare Organizations Choose HIPPA One®
Get a HIPAA One Demo
Additional Resources

Blog

Cybersecurity Checklist

Case Study
A HIPAA risk assessment tool is a resource or software designed to help organizations assess and manage the risks associated with the handling and safeguarding of protected health information (PHI) as required by HIPAA. Organizations that handle PHI, such as healthcare providers, health plans, and business associates, are obligated to conduct regular risk assessments, and a HIPAA SRA tool typically provides a structured framework to evaluate various aspects of an organization’s operations, systems, and policies related to PHI.
Yes, conducting a HIPAA risk assessment is required annually under the HIPAA regulations. The HIPAA Security Rule mandates covered entities and their business associates to perform regular risk assessments. In addition to the annual requirement, it is essential to note that risk assessments should also be conducted whenever significant changes occur in the organization’s environment, such as the implementation of new technologies, changes in policies or procedures, or other factors that may impact the security of PHI.
While the specific questions may vary based on the organization’s size, complexity, and nature of operations, here are some common types of questions that may be included:
- Administrative Safeguards:
- Does your organization have written policies and procedures in place to ensure HIPAA compliance?
- Are designated HIPAA privacy and security officers appointed within your organization?
- Has the workforce received appropriate training on HIPAA policies and procedures?
- Are there mechanisms for conducting regular audits and monitoring compliance?
- Physical Safeguards:
- Is access to PHI restricted to authorized personnel through appropriate physical controls (e.g., locks, access cards)?
- Are workstations adequately secured to prevent unauthorized access to PHI?
- Is there a process for identifying and addressing potential security breaches, theft, or unauthorized access?
- Technical Safeguards:
- Are there user authentication mechanisms (e.g., passwords, two-factor authentication) in place to control access to PHI?
- Is PHI encrypted to protect against unauthorized disclosure?
- Are there mechanisms for regular system updates and patches to address known vulnerabilities?
- Policies and Procedures:
- Are there documented policies and procedures for managing and addressing security incidents?
- Is there a process for conducting regular risk assessments and addressing identified risks?
- Are business associate agreements in place with relevant third parties?
- Breach Response:
- Is there an incident response plan in place to address potential security breaches or unauthorized disclosures of PHI?
- Is there a process for notifying individuals and regulatory authorities in the event of a breach?
- Are there measures in place to mitigate harm and prevent future breaches?
Performing a HIPAA risk assessment involves a systematic process that helps evaluate an organization’s compliance with HIPAA regulations and identifies potential risks to PHI. Here are the general steps involved in conducting a HIPAA risk assessment:
- Gather Information: Collect relevant documentation, policies, and procedures related to PHI handling, security measures, incident response plans, and previous risk assessments.
- Identify PHI Assets: Identify all systems, processes, and locations where PHI is created, received, maintained, or transmitted within the organization.
- Conduct Risk Identification: Identify potential risks and vulnerabilities that could impact PHI’s confidentiality, integrity, and availability. This includes evaluating administrative, physical, and technical safeguards.
- Assess Current Security Measures: Evaluate the organization’s existing security measures and controls in place to protect PHI. This involves examining policies, procedures, access controls, employee training programs, encryption practices, and incident response capabilities.
- Determine Risk Likelihood and Impact: Assess the likelihood of potential risks occurring and their impact on PHI security if they were to materialize. This helps prioritize risks based on their severity. Evaluate Risk Levels: Assign risk levels to identified risks based on their likelihood and impact. This helps determine which risks require immediate attention and mitigation.
- Develop Mitigation Strategies: Determine appropriate actions and safeguards to mitigate identified risks. This may involve implementing additional security controls, revising policies and procedures, providing staff training, or enhancing technical measures.
- Implement and Document Controls: Implement the identified safeguards and controls and ensure appropriate documentation is created or updated to reflect these changes.
- Monitor and Review: Continuously monitor the effectiveness of the implemented controls and review the risk assessment periodically or as significant changes occur within the organization.
- Document the Risk Assessment: Maintain comprehensive documentation of the risk assessment process, findings, actions taken, and ongoing monitoring efforts. This documentation is crucial for demonstrating compliance with HIPAA requirements.
Because of HIPAA’s complexity, many organizations turn to HIPAA compliance experts or utilize specialized HIPAA security risk assessment tools to ensure a thorough and accurate risk assessment. The process should be tailored to the organization’s specific needs and conducted regularly to maintain compliance with HIPAA regulations.
