
Healthcare Security Risk Assessment (SRA)
A Better Way to Manage Your HIPAA Security Compliance
Our Security Risk Assessment (SRA) offering now combines Intraprise Health’s highly rated security services with the industry’s leading HIPAA SRA software platform, HIPAA One®, to deliver a complete SRA solution for healthcare.
Customers can now leverage our comprehensive SRA assessor services through HIPAA One’s software platform (built on the NIST Cybersecurity Framework). SRA customers can access our assessor’s notes and findings through the HIPAA One platform. During and upon completion of the assessment, auto-generated reporting, including the final report of findings, as well as HIPAA One’s remediation management module can be utilized for an enterprise-wide, full-lifecycle and scalable approach to HIPAA security and compliance.
Healthcare SRA Process
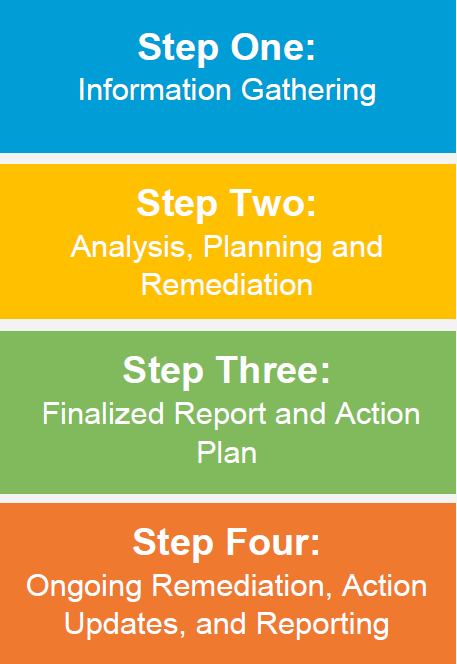
During the course of a Security Risk Assessment we will:
- Map vulnerabilities identified to both HIPAA (as amended by HITECH and the Omnibus 2013 Final Rule), NIST Cybersecurity Framework and the HITRUST CSF
- Ensure HIPAA Compliance
- Draft a comprehensive Report of Findings incorporating practical, real-world remediation recommendations
- Present findings and recommendations in stakeholders’ briefing session(s)
- Provide subject matter expertise for senior management decisions, regarding risk
- Assist with alignment of strategy, business objectives, and information assurance
We provide the structure, detail, and clarity you need to:
- Evaluate HIPAA/HITECH compliance
- Document current state of security controls
- Meet the requirements associated with Meaningful Use
- Identify gaps that pose true business risk
- Create a practical remediation roadmap
- Establish a sustainable operating model for information security and privacy
Healthcare SRA Engagement Types
Self Assessment
Independently Conduct your Risk Assessment
Self SRA Includes:
- Kick-Off call
- Assessor Support
- Access to policy and procedure template library
- Customer independently conducts assessment & remediation planning
- Customer signs final report
Facilitated Remote Assessment
Online Assistance to Conduct your Risk Assessment
Remote SRA Includes:
- Kick-Off call
- Assessor Support
- Access to policy and procedure template library
- Assessment responses and remediation plan reviewed by Assessor
- Assessor signs final report
Validated Assessment
Assessor-led Risk Assessment
Validated SRA Includes:
- Evidence based findings validated by Assessor
- Historical trend analysis of previous HIPAA PBRA’s
- Online walk-through practice
- Criticality levels based on Common Vulnerability Scoring System (CVSS)
- Executive and Technical Presentation
- HIPAA Security Risk Assessment (optional)
Additional Information
CONTACT US
Ready to get started? Have questions for our HITRUST, HIPAA or security teams?
We’re happy to help.
